PIA or DPIA: What’s the Difference?
Cyberspace is filled with vast amounts of personal information, from formal requests submitted to online service providers to various other personal details that users share across different internet platforms. Such sensitive information has always been a sought-after target for cybercriminals, and it is crucial to ensure its protection. This requires a comprehensive legal approach that incorporates a privacy impact assessment or data protection impact assessment.
What is a privacy impact assessment and data protection impact assessment?
In order to understand the main difference between DPIA and PIA, let’s first give these concepts clear definitions.
What is a PIA?
Privacy Impact Assessment (PIA) is a systematic process designed to identify and assess the potential privacy risks associated with a specific project, program, or system. The goal of a PIA is to evaluate how the collection, use, disclosure, and handling of personal information may impact individuals’ privacy rights and to ensure that appropriate measures are in place to mitigate any potential risks.
What is a DPIA?
Data Protection Impact Assessment (DPIA) is a specific type of privacy assessment that focuses on the risks and potential impacts of processing personal data, particularly in the context of new projects or systems. The DPIA process is mandated by data protection regulations, such as the General Data Protection Regulation (GDPR).
What is the difference between PIA and DPIA?
The Privacy Impact Assessment (PIA) is a process used to protect privacy by design when an organization starts or acquires a new business, implements a new process, or launches a new product.
The Data Protection Impact Assessment (DPIA) is an ongoing process, regularly applied to personal data processing, identifying, and mitigating risks. The DPIA is a part of the European Union (EU) General Data Protection Regulation (GDPR) compliance activities.
Check the main differences between DPIA vs PIA in the table below.
| Aspect | Privacy Impact Assessment (PIA) | Data Protection Impact Assessment (DPIA) |
| Scope | Broad assessment, considering overall privacy impact | Specifically focuses on the processing of personal data |
| Regulatory Basis | Often a best practice, voluntary in many cases | Legally mandated under data protection regulations (e.g., GDPR) |
| Focus on Personal Data | Considers a wider range of privacy concerns | Concentrates on the processing of personal data |
| Triggering Events | Good practice may not be legally required | Typically required before high-risk processing activities |
| Legal Compliance | Good practice, may not be legally required | Legally mandated in specific situations, non-compliance may lead to penalties |
| Documentation | Documentation varies based on organizational preferences | Requires specific documentation according to data protection laws |
| International Applicability | Used globally, not tied to specific data protection laws | Primarily associated with specific data protection regulations (e.g., GDPR) |
Compliance Aspekte is an integrated GRC solution that combines ISMS, DPMS and risk management tool in one single software. At Compliance Aspekte, we can provide you with a ready-to-use data protection kit.
Simplify DPMS implementation with Compliance Aspekte
Compliance Aspekte Data Protection Kit is a ready-to-use solution that simplifies DPMS implementation in organizations. The solution will enable quick and efficient management of the data protection systems with preinstalled PIA reporting options and much more.
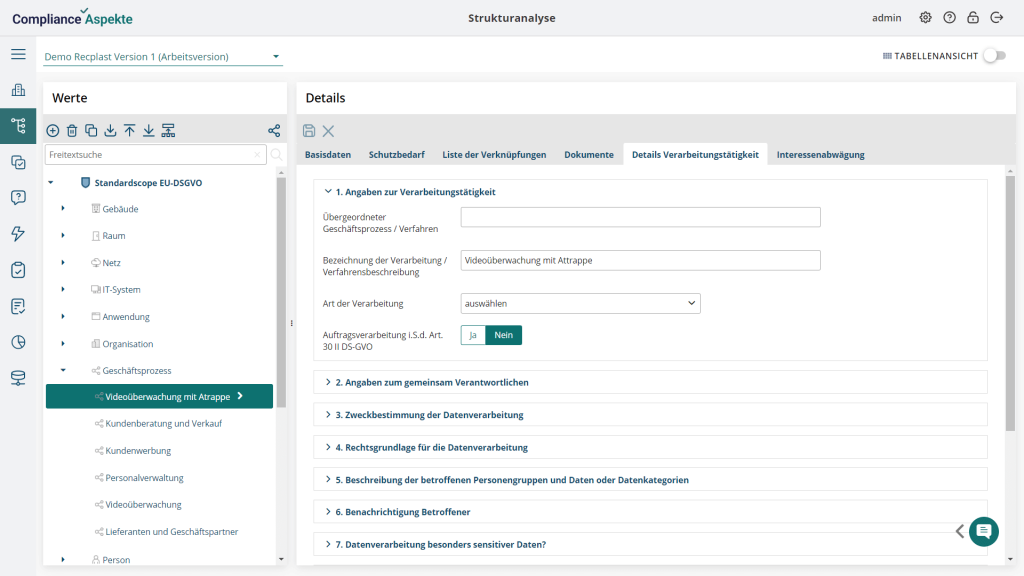
By using Data Protection Kit, you will get:
- Predefined typical organizational structure
- A list of processing activities required by the GDPR
- Pre-made PIA and ROPA reports
- Catalogs of relevant threats and controls
- Records of processing activities report
What are the key fundamentals of PIA and DPIA?
The basic principles of PIA vs DPIA are similar. It is an iterative cycle of four sequential stages:
- Defining the context of personal data processing;
- Establishing controls to ensure compliance with the fundamental principles;
- Assessing associated privacy risks;
- Validating the attained data protection level.
Key items you need to define during each stage of a PIA or DPIA:
- The parties (data controllers, processors, and subjects);
- The data nature and scope;
- The purposes of data processing;
- The compliance requirements under GDPR and/or other legislation.
When is a DPIA Required under GDPR?
The EU GDPR requires companies to perform a DPIA before specific data processing types to ensure they can mitigate risks. Article 29 of the EU Working Party Guidelines for GDPR lists activities eligible for DPIA. Some of the data-related events that may trigger a DPIA:
- Likelihood of high risks to data subjects’ rights and freedoms.
- Introduction of new data processing processes, systems, or technologies.
- Implementation of extensive systematic profiling with essential effects.
- Large-scale processing of criminal offense info or special category data
- Systematic monitoring of publicly accessible places on a large scale.
Some EU member states (and the UK) create national ‘Blacklists’ and ‘Whitelists’ to guide which processes do and do not require DPIA. Compliance Aspekte will help you identify relevant requirements in the countries in which you operate:
- Data subject evaluations. Information used to determine an individual’s work performance, financial situation, health, personal preference, behavior, etc.
- Automated decision making. Automated decision-making processes that could affect a data subject from a legal standpoint or in ways that could significantly impact the individual, such as exclusion or discrimination.
- Sensitive data processing. Activities that process sensitive data like political opinions, medical records, criminal convictions, etc.
- Processing for vulnerable data subjects. Vulnerable data subjects include children, immigrants, the elderly, and patients.
When is PIA required?
The PIA is a comprehensive analysis of how PII (personally identifiable information) is collected, stored, shared, managed, and protected. Companies must start PIAs early in project development or design and consider them throughout the lifecycle with the privacy impact assessment template.
Data processing activities that may lead to a PIA:
- Conversion of paper-based records to electronic systems.
- Changes of anonymous information to non-anonymous.
- New implementation of existing IT systems (i.e., application of new technologies).
- Essential merging of databases holding sensitive information.
- New public access to user-authenticating technology (e.g., password, digital certificate, biometric).
- Information is obtained from commercial or public sources.
- New uses of information between data processing agencies (e.g., cross-cutting E-Government initiatives).
- Changes in a business process that result in new uses or disclosures of information.
- Addition of new information to the collection.
What do companies need to conduct a PIA or DPIA?
To carry out a PIA or DPIA effectively, companies need to engage in a series of structured steps:
- Gathering information. Start by collecting relevant data and details about the processing activities.
- Engagement with internal teams and specialists. It’s important to discuss with team members and internal experts who understand the nuances of the project.
- Understanding legal and regulatory obligations. Review the laws and regulations that apply to the data processing activities.
- Evaluating the legality and necessity. Check if the activity is legal, transparent, necessary, and in proportion to the aims.
- Spotting and ranking potential issues. Identify any problems or gaps in compliance and assess their impact.
- Seeking advice from external authorities. If needed, consult with external experts, including regulatory bodies.
- Developing risk mitigation strategies. Suggest ways to minimize risk through technical, contractual, or organizational changes.
- Finalizing and approving the plan. Get the required approvals for the outcomes and the plans to address them.
- Implementing the mitigation plan. Put the agreed-upon plans into practice.
- Regular review and update. Schedule times to revisit and update the PIA/DPIA, especially when there are changes in how the data is used.
These steps serve as a broad guide to help organizations perform these assessments effectively, and it’s recommended that companies stay flexible in their approach to conducting PIA and DPIA.
How to prepare for a PIA?
Getting ready for a Privacy Impact Assessment (PIA) involves gathering detailed information about your data processing activities.
To illustrate, when the U.S. Securities and Exchange Commission carries out a PIA according to the E-Government Act of 2002, it records several key details:
- Types of personal data processed. Understand the nature and categories of personal data being handled.
- Purpose of data collection. Clearly define why the personal data is collected and for what specific purposes.
- Data sharing practices. Outline the methods used for sharing data both within the organization and with external parties.
- Consent and notification procedures. Detail how individuals are informed about the data collection and the process for obtaining their consent.
- Data security measures. Describe the current safeguards in place to protect the data from unauthorized access or breaches.
It’s important to note that no single person holds all the knowledge needed for a thorough PIA. The focus of your assessment determines who should be part of the information gathering. For instance, if the assessment is aimed at optimizing a complex marketing technology platform for the Marketing department, then a marketing manager would be best suited to provide insights into the business objectives and challenges that the platform addresses.
How to Prepare for a DPIA?
Organizations governed by GDPR must engage in thorough fact-finding, which, while universally necessary, will differ based on each organization’s unique context.
In preparing for a GDPR DPIA, it’s essential to:
- Detail processing activities and their purposes. This includes explaining the data processing actions and their objectives, as well as any legitimate interests of involved third-party controllers.
- Assess the necessity of data processing. Evaluate the importance of these activities in relation to their stated purposes.
- Identify risks to individuals’ privacy. Spot potential privacy issues that might affect the rights and freedoms of those whose data is being processed.
- Define privacy safeguards for high-risk data. Outline the measures in place to handle privacy risks associated with processing data considered high-risk under GDPR.
- Show GDPR compliance. Demonstrate how the organization’s practices align with GDPR, especially in protecting the rights and interests of data subjects.
The process of gathering DPIA information under GDPR mirrors that of a PIA in several ways:
- Contextual project proposals or briefs. These provide vital business context.
- Identifying concerned individuals. This includes distinguishing between customers and employees.
- Types of personal data processed. This could range from contact details to online behaviors.
- Handling sensitive data. Acknowledge any particularly sensitive data, such as precise locations.
- Data sources. Identify where the data comes from, like account creation or tracking cookies.
- Scope of processing activity. Determine whether the processing is local, international, or otherwise.
- Third-party involvement. Document any involvement from vendors, business partners, or other business areas.
- Relevance of privacy policies. Consider the impact of privacy policies on the activity.
- Contractual obligations. Understand what the organization’s contracts say about the data processing activity.
- Existing measures. Note that the technical and organizational measures are already in place.
How to simplify the process of managing PIA and DPIA?
How can you simplify the process of managing PIA and DPIA along with other standards?
Compliance Aspekte GRC platform is a solution designed explicitly for implementing multiple data protection and information security regulations. Here are the main benefits of the Compliance Aspekte tool:
- ISMS tool & DPMS tool in one single platform
- Co-pilot based on Azure AI GPT technology.
- External data protection officer (DPO) as a service.
- Integration with third-party systems like GSTOOL, EXCEL, CMDB, Jira, Microsoft, SAP, asset management software, and others.
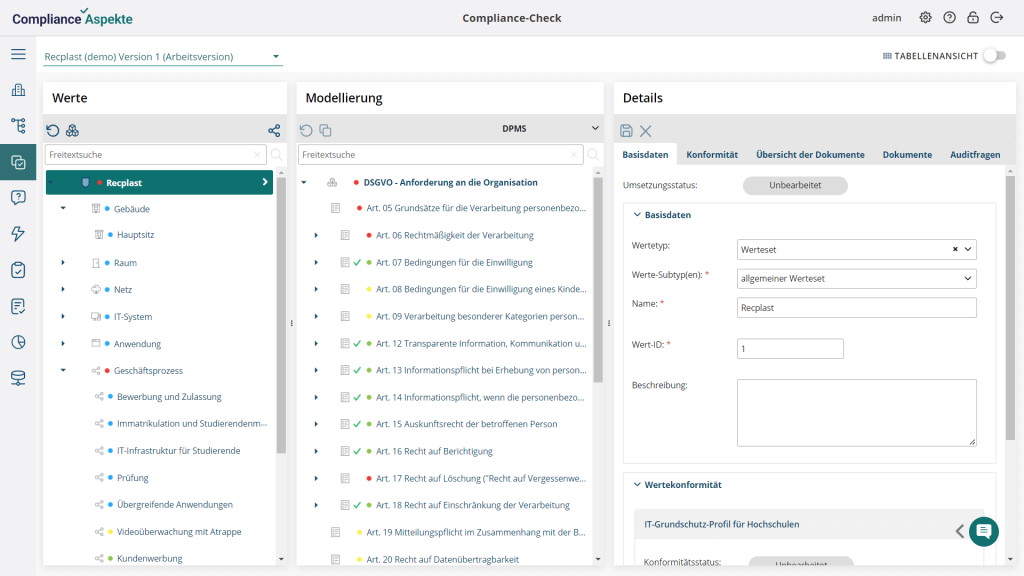
Contact us today to find out more about our compliance platform capabilities. Our team will be happy to guide you through the platform’s functionality and general operation.
At Compliance Aspekte, we also provide data protection consulting services that include:
- DPMS as a service: We help companies recognize risks, create policies, and keep improving their security.
- Data protection analysis: We thoroughly examine your data processes to spot potential risks.
- Data protection implementation: We create tailored data protection policies for your company and help train your staff.
- Data protection monitoring: We regularly update and review your data protection strategies to keep them current.
- External data protection officer: Our experts are well-versed in the latest data protection laws, ensuring your compliance and solving compliance challenges.
- Support line: Available from 9 am to 6 pm, our support line helps you quickly resolve any information security and data protection issues.
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
