
 Profile for Universities
Profile for Universities
IT-Grundschutz Profile is the modification of the information security standard that includes recommended security measures. Organizations can further develop their own university-specific security concept, and build ISMS based on the standard protection level. We have developed an IT-Grundschutz tool – Kit for Universities – that helps CISOs and DPOs to establish and maintain ISMS and data protection management quickly, effortlessly, and budget-savvy.
Challenges of Establishing an ISMS
- Distributed organizational structures
- Unclear responsibilities
- Lack of accuracy of ISMS implementation
- Incomplete documentation
- Using outdated tools, e.g., Excel, instead of ISMS solutions
IT-Grundschutz Profile Overview
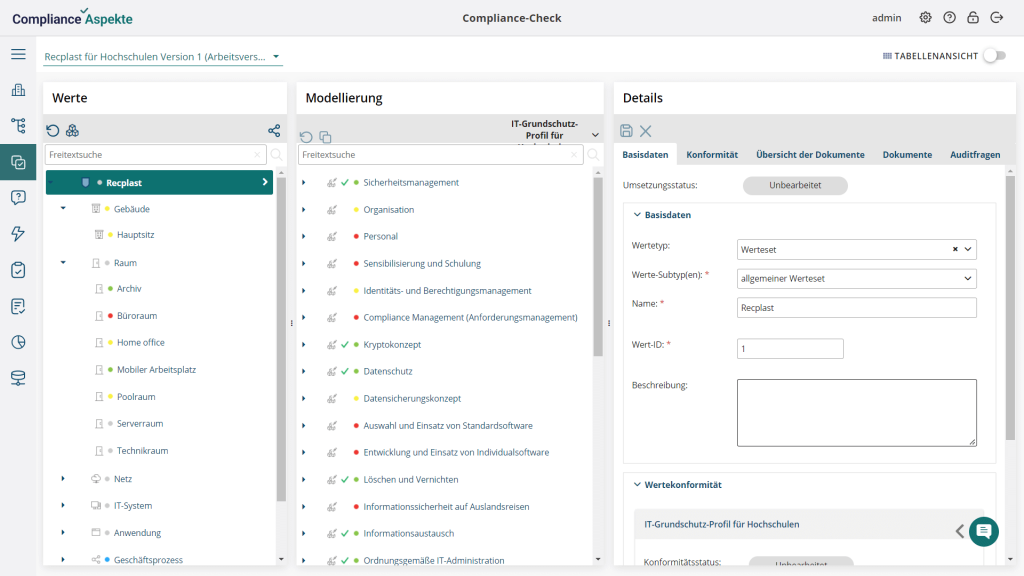
IT-Grundschutz profile for universities consists of 83 modules (out of 94), among which:
- 31 Process modules, higher-level modules as an overview assigned to the entire information network
- 52 system modules, assigned to the target objects in process maps.
How to Implement IT-Grundschutz Profile with the ISMS Management Software
Compliance Aspekte Kit for Universities enables working with ISMS and DPMS simultaneously in one place and offers clear and simple modeling of the concepts.
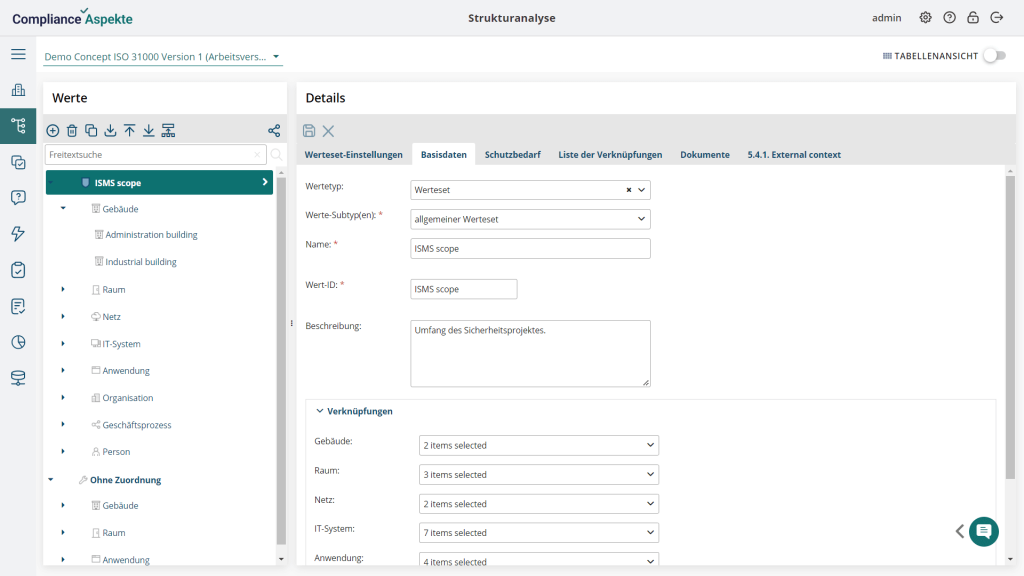
- Implementation of the process map (applications and IT and Building Infrastructure) with clear assignment of building blocks of the IT-Grundschutz Compendium for universities.
- Basic-, standard-, core protection levels of protection.
- Determination of protection requirements.
- Integration with I-doit.
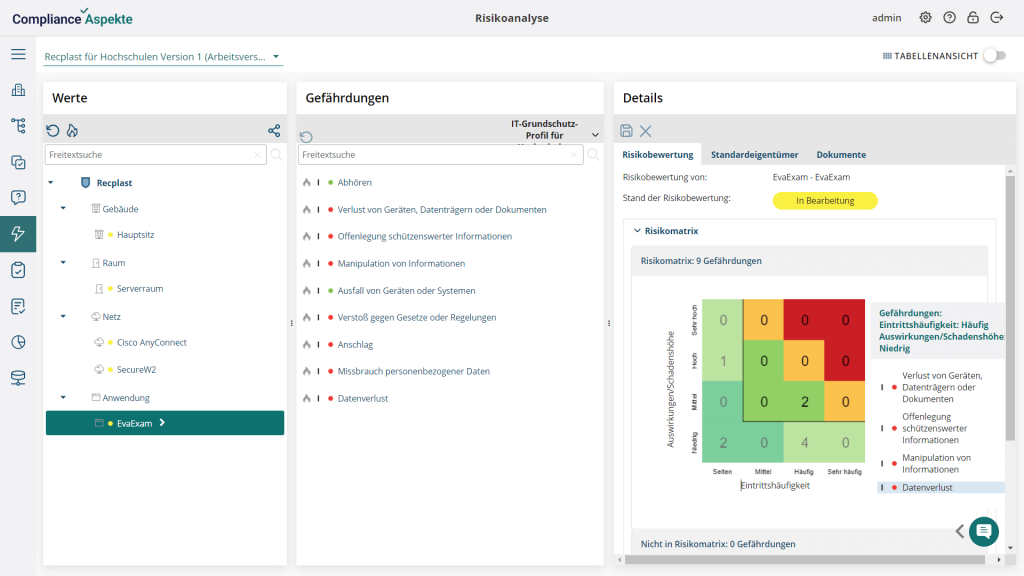
- Individual risk assessment in case of high protection needs.
The system offers implementation recommendations for the application of the individual building blocks in the university, such as the implementation notes of IT-Grundschutz or custom implementation recommendations, e.g., for those of representatives of the member institutions in the working group Information Security of the ZKI).
Effective and easy-to-use IT security management system based on the latest standards and regulations — from planning and establishing the security concept to certification.
