Official GS tool alternative
Ready-to-go IT-Grundschutz kit
Automatic migration to IT-Grundschutz Compendium 2023
Hosted in Germany
Why choose the Compliance Aspekte IT-Grundschutz tool
Try for free- One-click migrations to new BSI Grundschutz Compendiums.
- A single platform for multiple information security, IT, and data protection regulations.
- Seamless integration with systems like GSTOOL, EXCEL, CMDB, Jira, Microsoft, SAP, asset management software, and other systems.
- Personal AI assistant based on Azure AI.
- Framework for covering industry-specific security standards (B3S) as well as IT-Grundschutz profiles.
- IT-Grundschutz kit with all the ready-to-use structure, necessary tools, documentation, and guidelines.
- Standard reports generation according to IT-Grundschutz (A1-A6).
Discover the IT-Grundschutz tool in action
Try for freeHow to implement
IT-Grundschutz
with Compliance Aspekte
At this stage, Compliance Aspekte supports users with several essential steps and functionalities.
- Creation of structural analysis of your organization, including the business processes, buildings, applications, and IT systems, via an inventory check of your assets/values.
- Order and grouping in a hierarchical asset structure and visualization of the linking by assigning types.
- Determination of protection needs and automatic inheritance of requirements (maximum principle, including cumulation and distribution effects).
- Definition of additional user-defined protection goals, besides integrity, availability, and confidentiality, e.g., B. Industry or company-specific goals.
- Adjustments to the depth of information (attributes) of your assets using custom fields.
- Presentation of assets in the table view, including the ability to edit data (bulk-edit), arrange, group, sort, filter, and export to Excel or CSV format.
- Standard A1 reporting with information on asset name, type, subtype/s, description, and links.
- Standard A2 reporting with information on asset protection needs.
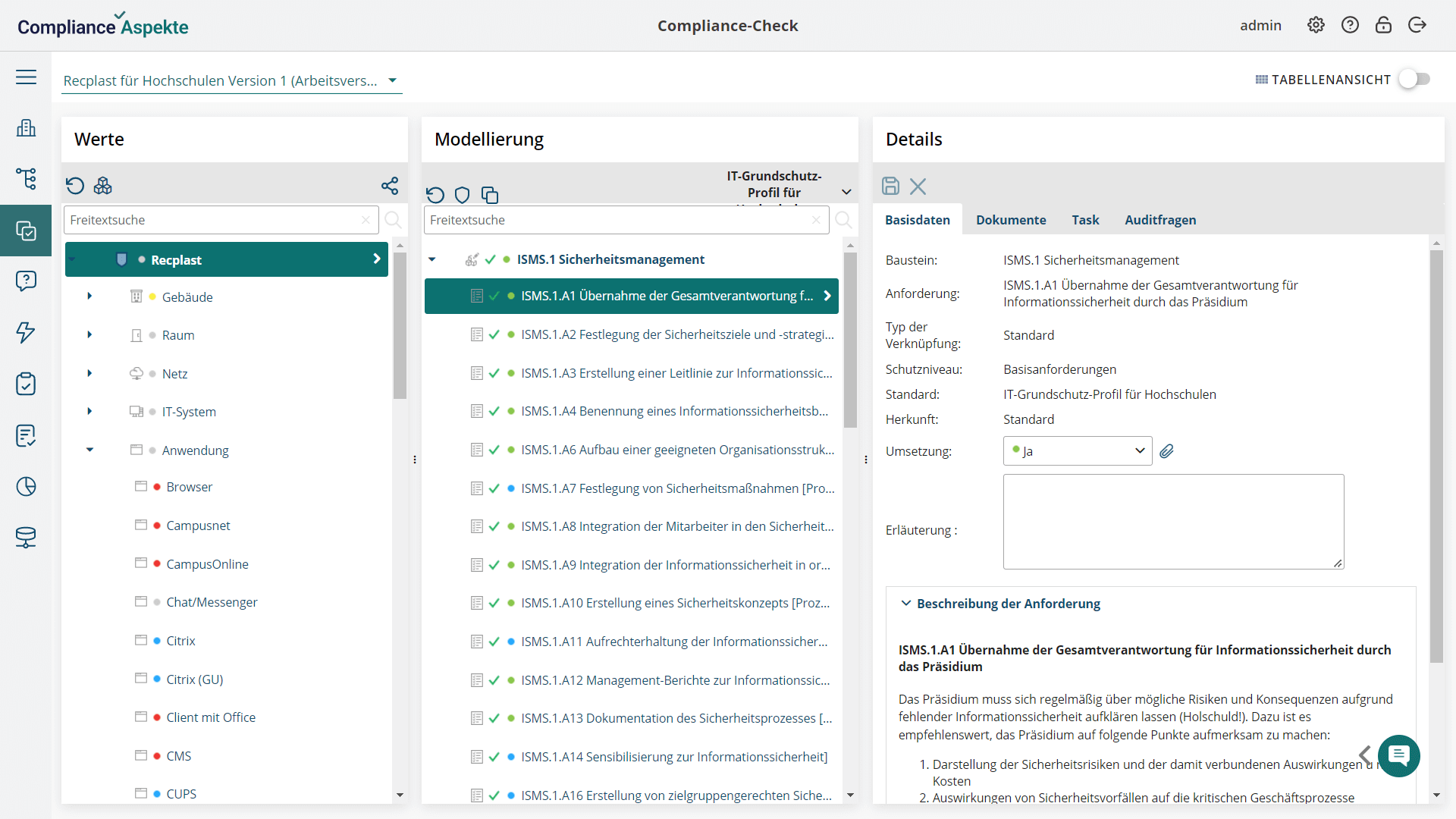
At this stage, you can define the security requirements and fully model your concept. Here, you prepare the details for the test plan and carry out the IT baseline protection check (compliance test).
- Automatic assignment of IT-Grundschutz modules, recommended requirements, and safeguards.
- Monitoring the implementation status of defined measures, requirements, and overall compliance status of assets.
- Bulk data processing (bulk edit), e.g., changing the realization status of requirements and measures for several assets.
- Assignment of persons responsible for task fulfillment and control.
- Data visualization in the table view with different perspectives (e.g., grouping by IT systems with unimplemented data backup requirements).
- IT baseline protection profile for universities.
- Standard reports A.4 Result of basic Compliance Check and A.6 Implementation plan.
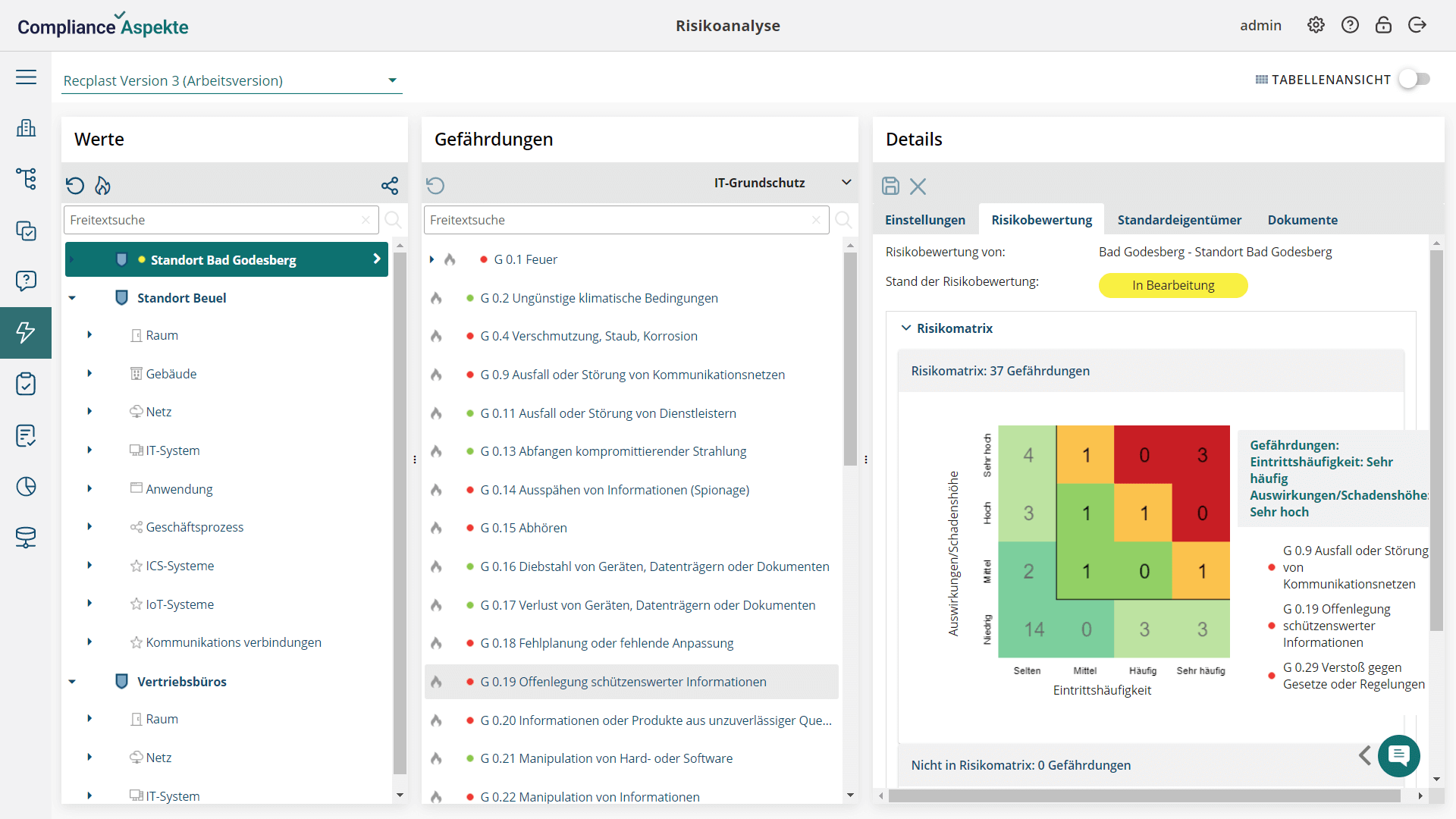
Using Compliance Aspekte software, you can conduct in-depth risk analysis to make more informed decisions.
- Qualitative risk analysis, according to IT-Grundschutz 200-3, which is a simpler methodology compared to conventional risk analysis methods.
- Automated risk analysis for assets with high and very high protection requirements.
- Available risk catalog based on the BSI G0 list with 47 elementary threats and with the possibility of creating user-defined threats.
- Risk matrix (4×4 or 5×5 dimension) to show the frequency of occurrence, damage effects, and risks.
- Allocation of additional measures to the hazards and their monitoring, as well as the associated requirements.
- Standard A5 reporting with information on risk analysis.
What is new in the BSI Grundschutz Compendium 2023
- CON.11.1 Secret protection VS-ONLY FOR SERVICE USE (VS-NfD)
- OPS.1.1.1 General IT operations
- OPS.2.3 Use of outsourcing. This module replaces OPS.2.1 outsourcing for customers.
- OPS.3.2 Offering outsourcing. This module replaces OPS.3.1 Outsourcing for service providers.
- APP.5.4 Unified Communications and Collaboration (UCC)
- SYS.1.2.3 Windows Server
- SYS.1.9 Terminal Server
- SYS.2.5 Client Virtualization
- SYS.2.6 Virtual Desktop Infrastructure
- NET.3.4 Network Access Control
- SYS.2.2.2 Clients on Windows 8.1. Support for the operating system ended on January 10, 2023. Windows 8.1 should, therefore, no longer be used.
- OPS.2.1 Outsourcing for customers. The module is replaced by OPS.2.3 Use of outsourcing.
- OPS.3.1 Outsourcing for service providers. The module is replaced by OPS.3.2 Offering outsourcing.
Compliance Aspekte IT-Grundschutz kit
This kit provides users with all the ready-to-go structure, necessary tools, documentation, and guidelines needed to implement an ISMS yourself and meet IT-Grundschutz compliance.
Using Compliance Aspekte IT-Grundschutz kit, you will get:
- ISMS Concept model: preset typical company infrastructure – choose only relevant assets without creating them from scratch.
- Automatic assignment of requirements according to IT-Grundschutz.
- Predefined levels of protection that you can choose and easily switch between them (Basic, Standard, Core).
- Automatic calculation of the conformity status.
- Analytical table view with bulk editing options.
- Risk analysis and assessment using a risk matrix.
- All the basic reporting templates you need.
Compliance Aspekte is trusted by
Testimonials
We were new to compliance and ISO 27001 implementation and had to go through the sophisticated certification process. Puzzled by the regulatory complexity, we wanted to find the best way for us to get started. Our project manager (aka security officer) had never worked with such compliance aspects and rules before. So we decided to get third-party assistance and signed up with Compliance Aspekte. Their guided approach has played a vital role for us. They had all the detailed explanations for compliance checks and risk analyses, including suggestions on how to handle it practically.
One of the features we like best about Compliance Aspekte is its streamlined compliance process. At every stage during the security management lifecycle process, recurring tasks like scoping, structural analysis, modeling, and even tracking risks and controls are supported by a variety of features, e.g. mapping controls with multiple requirements, assigning individual assets to different scopes as well as expanding requirement and control catalogs. Having Helga, the compliance assistance bot, is also a very special plus as she can explain terms and provides guidance through the application. We really love and live Compliance Aspekte!
Compliance Aspekte is very user-friendly and customization is easy. We can conduct ISO compliance, and data protection…we can make anything we want in one tool. And this is the only tool with which it is possible. It helps us to keep the data consistent and simplify audits. The Compliance Aspekte tool is better than the existing competitors on the market and at the same time cheaper.
Try Compliance Aspekte for free
FAQ

BSI IT Grundschutz is a collection of standards and catalogs that describe generalized procedures for protecting information technology. The aim of the IT-Grundschutz is to describe the minimum requirements for the normal protection needs of IT applications and IT systems.
Modules are the elementary components of the Grundschutz methodology. They contain the essential requirements and recommendations for securing individual or complex systems and processes and are published in the BSI Grundschutz Compendium.
BSI IT Grundschutz and ISO 27001 are similar in approach. Both standards can be used to determine IT risks and reduce them to an acceptable level using suitable measures. ISO 27001 is more focused on managing information security, whereas the BSI basic protection catalogs describe detailed procedures for minimizing risks.
No, the implementation of the IT-Grundschutz measures is not obligatory. The standard has a recommendatory nature.
The BSI offers standardized processes and recommends measures to enable companies to meet the challenges of digitization and avoid cybercrimes confidently.
To do this, you can:
• Get the Compliance Aspekte IT-Grundschutz kit, which you can use to configure the system yourself.
• Contact us for a free consultation. Our experts will support you at every stage of implementing the tool in your organization.
Within Compliance Aspekte, the BSI IT Baseline Protection methodology is utilized to ensure compliance with IT security standards systematically. The software supports this by allowing users to define assets (or target objects) and apply the necessary controls and measures dictated by the BSI guidelines. This facilitates the organization’s ability to maintain robust IT security practices as outlined by BSI, integrating these practices into broader compliance and risk management frameworks.

Effective and easy-to-use IT security management system based on the latest standards and regulations — from planning and establishing the security concept to certification.