
 Architecture & Design
Architecture & Design
Compliance Aspekte is designed to automate and simplify the activities associated with corporate governance, compliance, and risk management. As a modern solution , it is developed using the latest industry practices for software development with the modern tech stack in its core (Angular, Java). The modularity of Compliance Aspekte allows us to flexibly customize the system to customer needs while ensuring “one system vision”.
Developing a GRC solution, we set top priority for product security. Our software engineers use SSDLC (Secure Software Development Lifecycle) methodology and other practices to assure product security. We also follow the main requirements of the following standards and methodologies: ISO 15408, ISO 27002, OWASP Risk Rating Methodology.
Our other priority is to develop a convenient and user-friendly solution. Our UX and UI engineers for interaction and visual design conduct the heuristic evaluation after Jakob Nielsen to assess the usability of the product after any changes have been implemented.
System Architecture
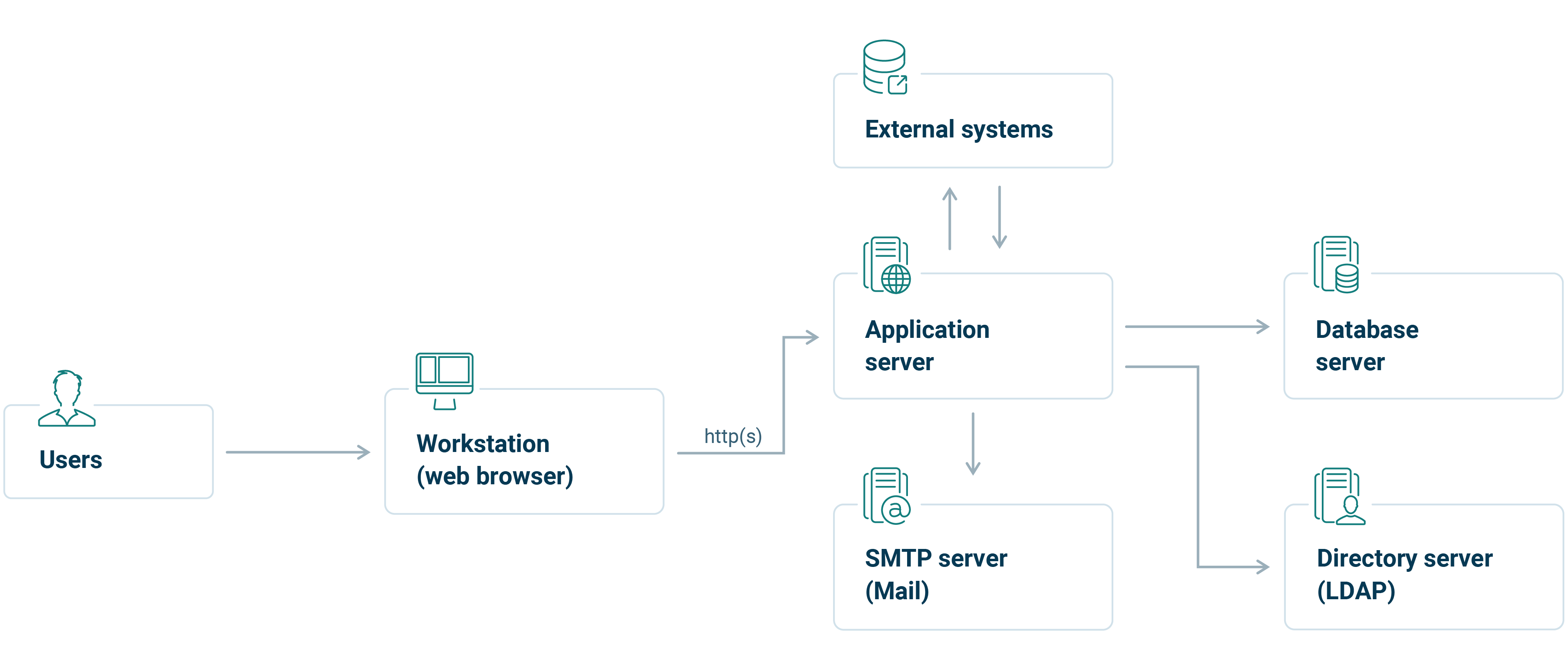
Platform
The application is implemented as a Java EE application compatible with Servlet container 4.0 specifications. By default, it is delivered with the Tomcat application server.
Configuration
Application configuration is made in property files.
Persistence
Data persistence is addressed using a relational database and JPA Object Relational Mapping layer (Eclipse Link).
Internationalization
All string resources are externalized to assure smooth localization. By default, the solution is delivered with the support of German and English languages.
Logging
Logging is implemented based on the Logback framework. The solution supports several levels of logging.
Performance
The system is responsive under much data – requirements, controls, threats, and the connections between them.
Scalability
The application is stateless in order to easily support horizontal scalability.
REST API
REST API is used for data interchange between client and server as well as for the integration with different systems (ServiceNow, SAP, etc.)
Security
Security is based on the JWT (JSON Web Token) flow. HTTPS certificates can be issued and then set up on the level of the servlet container (Tomcat) so that traffic between client and server parts of the solution is properly secured.
Hardware and system requirements
The following system requirements are recommended to guarantee the proper operation of Compliance Aspekte:
- CPU: Core i5
- HDD: at least 64 GB of free hard disk space (SSD recommended)
- RAM: at least 16 GB
- Operating system: Windows and Linux-based platforms
- Java
- Database support: Oracle, Microsoft SQL, and MySQL
Request more information about our solution and find out how our solution can address your specific security issue.
Effective and easy-to-use IT security management system based on the latest standards and regulations — from planning and establishing the security concept to certification.
