How Compliance Aspekte
simplifies NIS2 implementation
Contact us
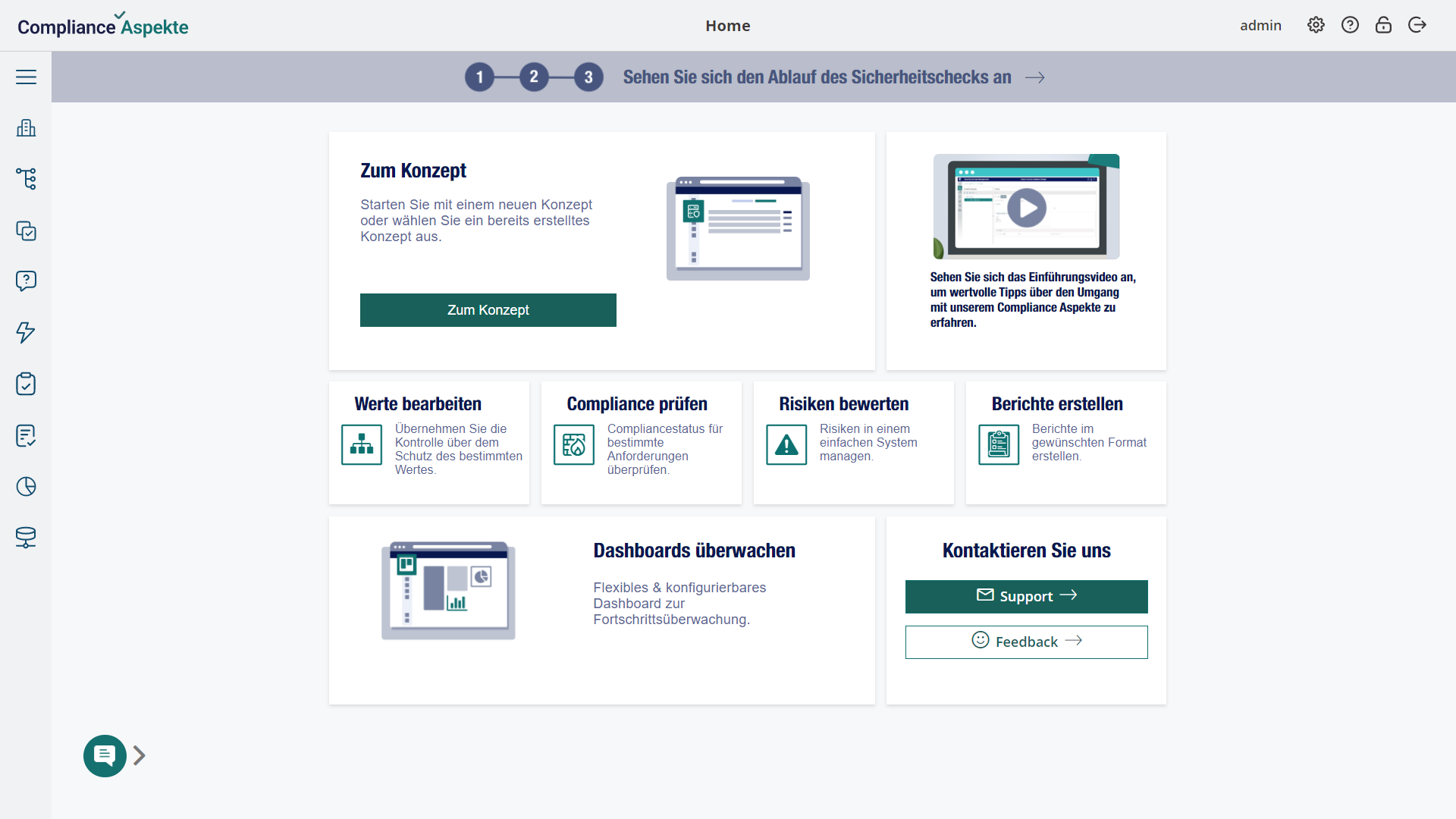
- Centralized compliance management: Compliance Aspekte consolidates ISMS, DSMS, Risk Management, and ESG Reporting into a single platform.
- Multi-standard compliance: Compliance Aspekte allows to manage multiple compliance standards simultaneously, including BSI IT Grundschutz, ISO 27001, GDPR, ASPICE®, ensuring that overlapping requirements are addressed efficiently and consistently across different frameworks.
- Consistent data: All compliance data, including assets, policies, procedures, risk assessments, and audit results, is stored in a single, unified repository. This avoids data inconsistencies and simplifies data retrieval for audits and reporting.
- External integrations: The system integrates with Microsoft Azure and SAP-based infrastructures, as well as CMDB systems like i-doit and Microsoft System Center, project management solutions like Jira, and more.
- AI Functionality: Compliance Aspekte offers AI features that can simplify compliance routines, provide guidance on NIS2 implementation, suggest tasks for implementing compliance controls, and help navigate complex documents.
- Collaborative functionality: Our NIS2 tool offers features that simplify collaboration within the information security department and with other stakeholders, including internal task management functionality, integration with Jira, alerts, and sharing access via links.
- Automation of compliance routines: Compliance Aspekte automates routine and repetitive tasks, reducing the burden on compliance teams and allowing them to focus on more strategic activities.
- Flexible report generation: The platform enables users to generate both standard and custom reports to meet specific regulatory requirements or organizational needs.
3 Approaches
to NIS2 Compliance
with Compliance Aspekte
Organizations can obtain user licenses for Compliance Aspekte as a software solution to manage their NIS2 compliance.
With this approach, companies get full control over the compliance processes as their internal teams use the platform’s features for asset management, risk management, compliance checks, report generation, and more. This model is perfect for companies with established compliance teams that need an effective tool to improve their compliance processes.
Our NIS2 experts provide customized compliance guidance and support to help the client to achieve NIS2 compliance.
This approach can cover GAP analysis, NIS2 implementation, consultations, trainings and all the needed NIS2 consulting support.
For companies interested in a turn-key package, we offer a fully managed NIS2 implementation service that includes taking care of the overall project.
From discovery and setting the Compliance Aspekte platform to managing and supporting all the compliance processes in the system, as well as assisting with all the arising tasks and issues.
Get started with NIS2 certification
Contact usFunctionality of the
NIS2 compliance software
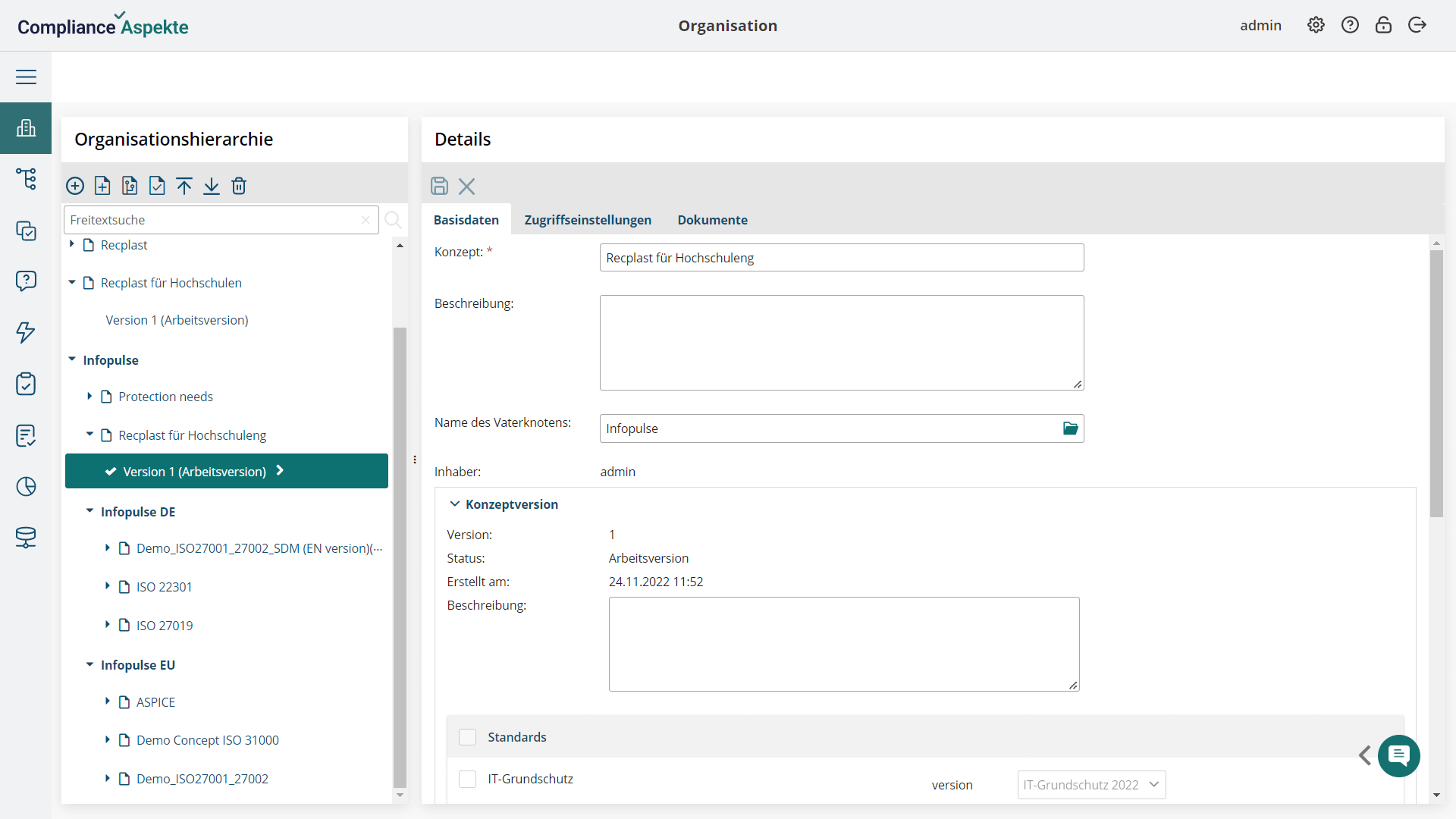
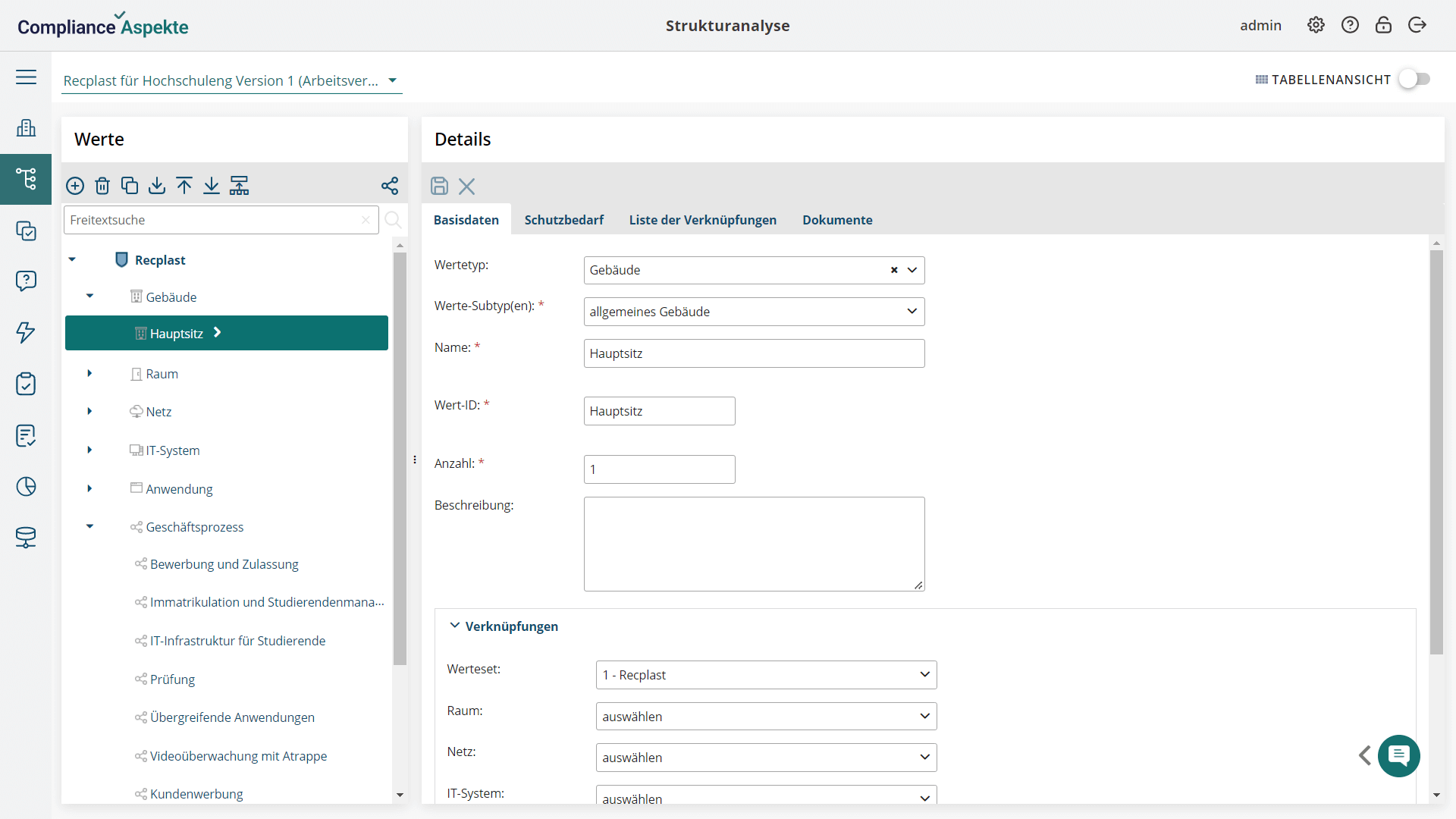
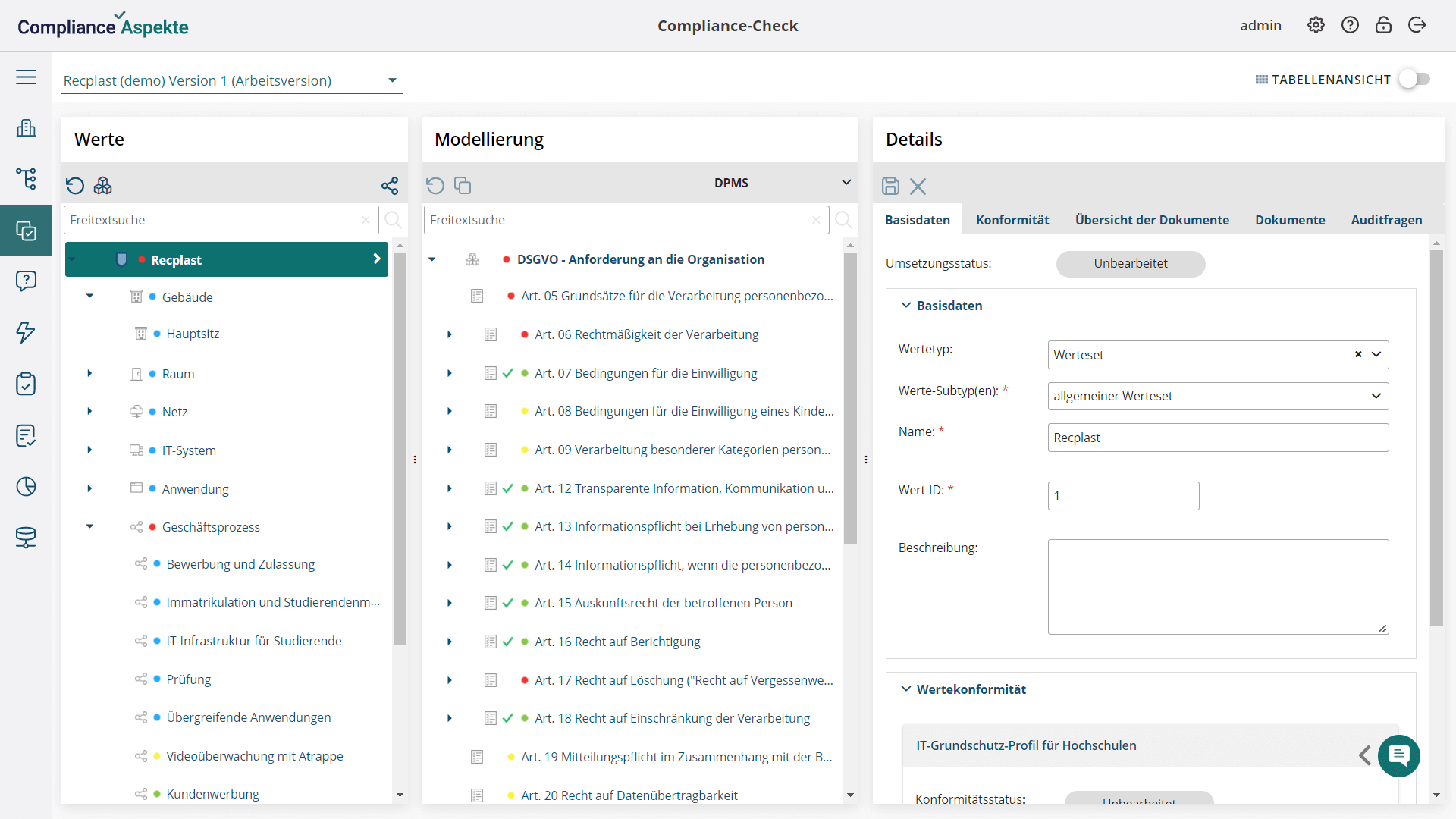
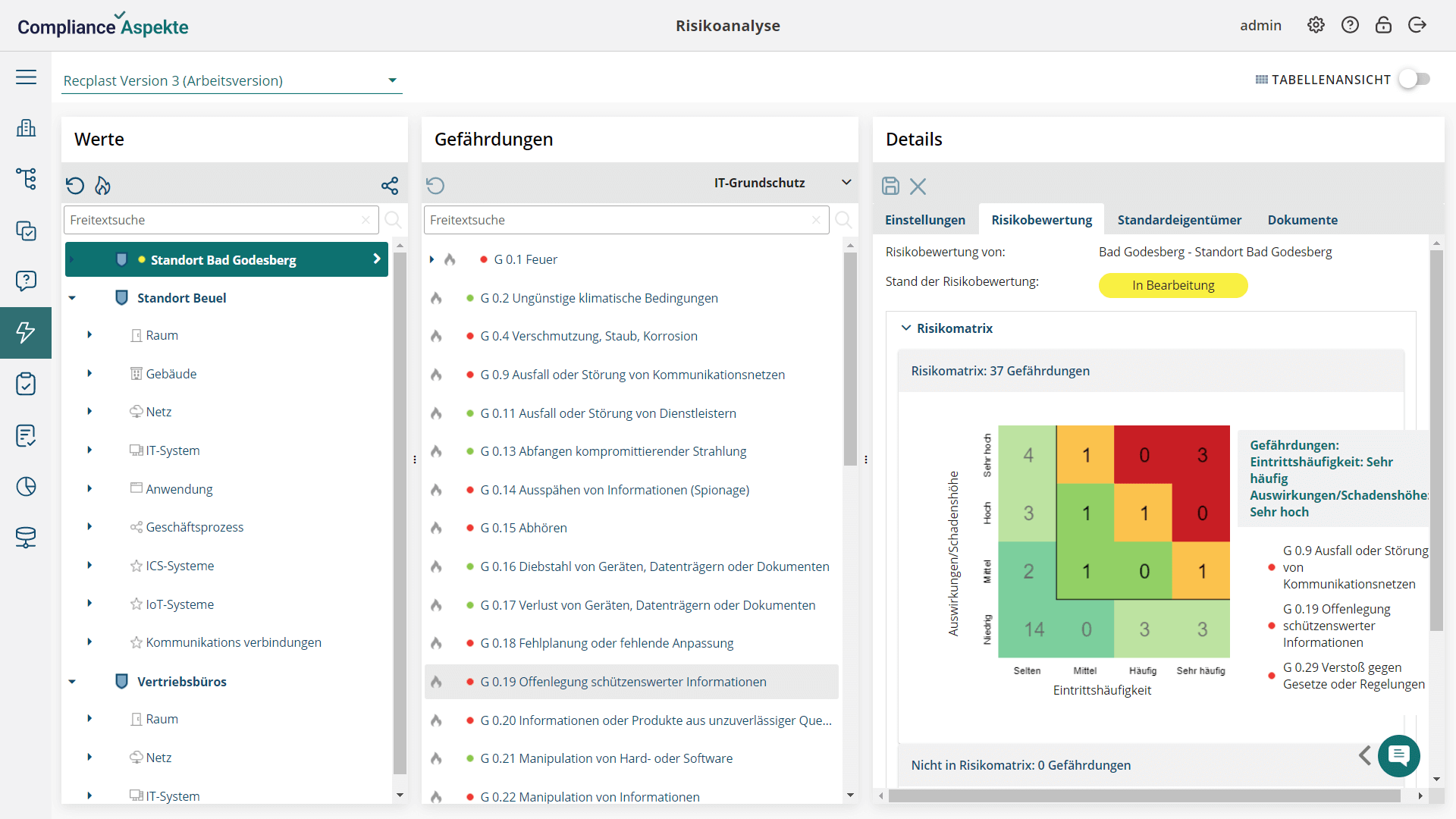
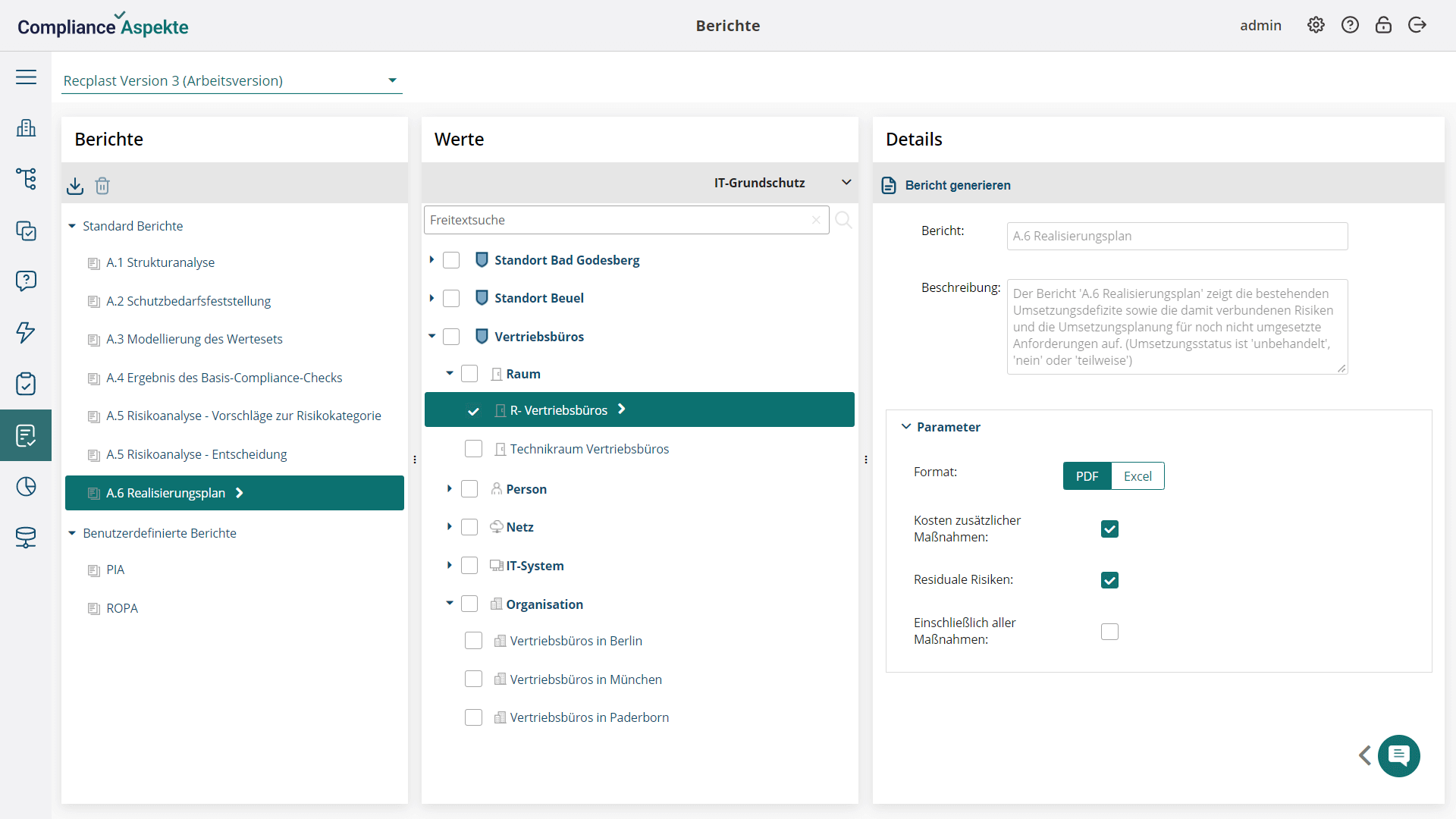
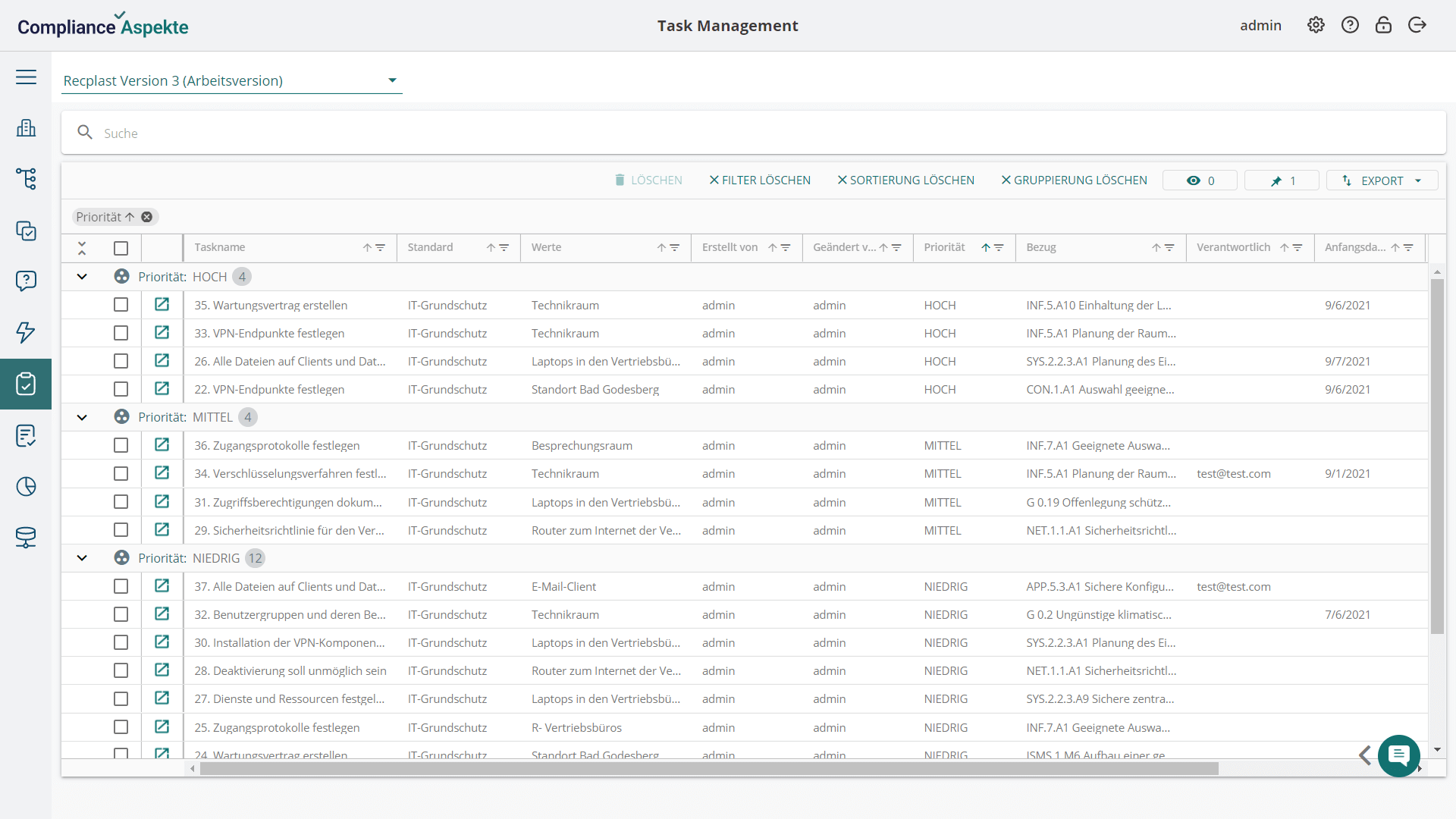
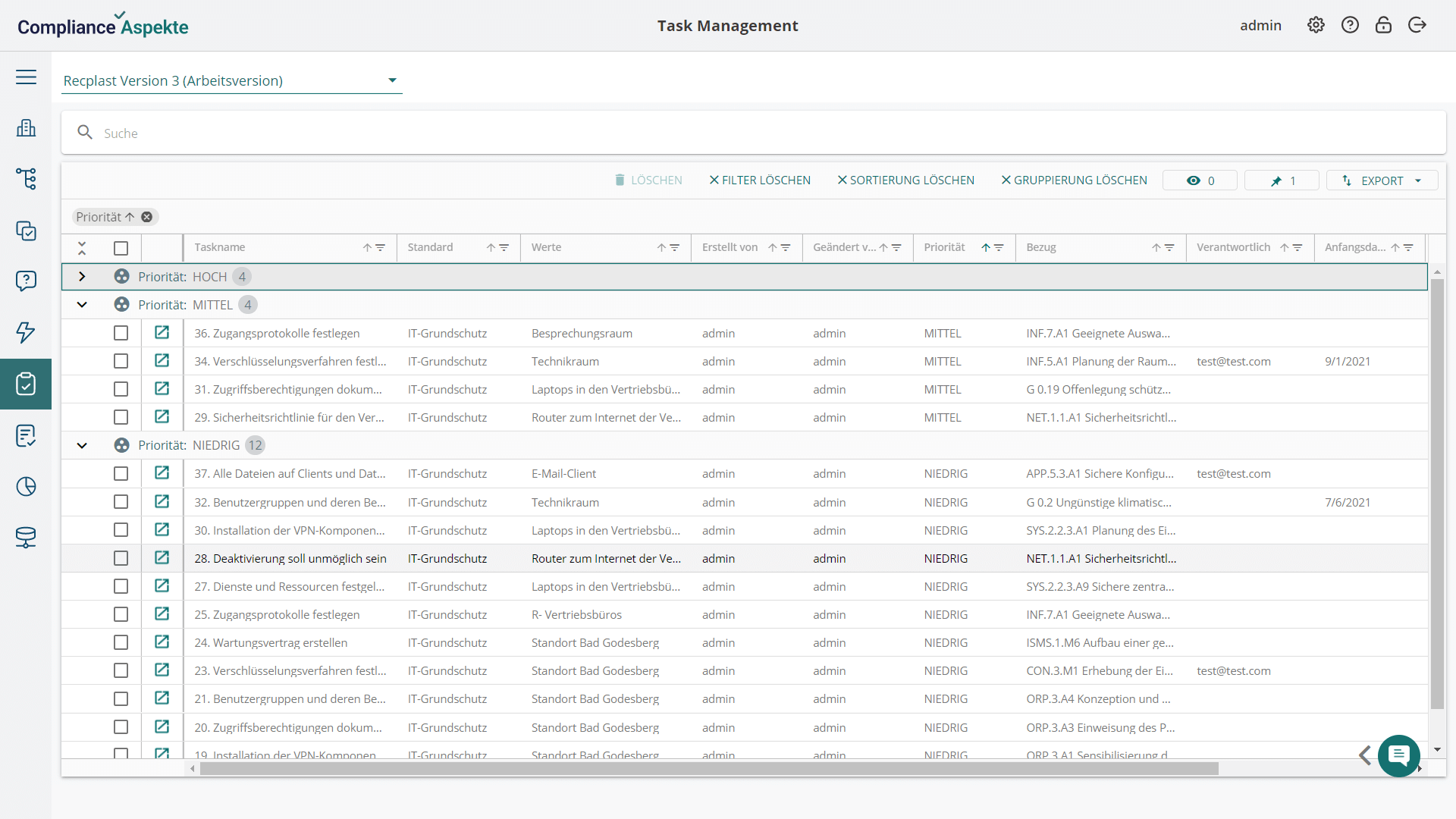
- Comprehensive structure representation: Visualize your organization’s entire structure, including all branches and units, in an intuitive tree model.
- Centralized data storage: Store all organizational data in one centralized location, ensuring easy access and management of information across the entire organization.
- Effortless asset exploration: Easily explore and investigate asset structures, connections, and relevant business processes using our information security tool.
- Custom attributes and classifications: Add custom attributes to assets, classify them by types and subtypes, and map specific objects as object classes.
- Seamless external integrations: Conduct external integrations to enhance functionality and data management within your information security framework.
- Multi-standard compliance management: Manage and evaluate multiple compliance standards and regulations within a single platform.
- Custom asset tree model: Build a custom asset tree model using the asset structure, enabling the evaluation of assets at different levels and accumulation at the top.
- Custom protection requirements: Create custom protection requirements and define custom levels for these requirements, tailored to your specific needs.
- Customizable risk matrices and assessment scales: Create and customize risk matrices and assessment scales to identify potential threats related to specific assets.
- Tailored risks and threats catalogs: Develop and manage tailored catalogs of risks and threats, ensuring precise identification and mitigation of asset-related threats.
- Automated report generation: Automatically generate compliance reports with our software, saving time and ensuring accuracy.
- Built-in Compliance Aspekte AI Copilot: Distribute generated reports effortlessly using the built-in Compliance Aspekte AI Copilot.
- External data analytics integration: Integrate with external data analytics systems to analyze data from the tool, enhancing insights and decision-making.
- Internal and external collaboration: Effectively collaborate with both internal and external users.
- Easy access sharing: Grant access to specific assets and data in Compliance Aspekte by providing secure links to external users.
- REST API integration: Seamlessly integrate Compliance Aspekte with other asset management and CMDB solutions such as i-doit, GLPI, FNT Command, Microsoft System Center, Microsoft SharePoint, and more.
- Defined Data Marts: Access application data directly from the database through several predefined Data Marts for efficient data retrieval and analysis.
Compliance Aspekte is trusted by
Testimonials
We were new to compliance and ISO 27001 implementation and had to go through the sophisticated certification process. Puzzled by the regulatory complexity, we wanted to find the best way for us to get started. Our project manager (aka security officer) had never worked with such compliance aspects and rules before. So we decided to get third-party assistance and signed up with Compliance Aspekte. Their guided approach has played a vital role for us. They had all the detailed explanations for compliance checks and risk analyses, including suggestions on how to handle it practically.
One of the features we like best about Compliance Aspekte is its streamlined compliance process. At every stage during the security management lifecycle process, recurring tasks like scoping, structural analysis, modeling, and even tracking risks and controls are supported by a variety of features, e.g. mapping controls with multiple requirements, assigning individual assets to different scopes as well as expanding requirement and control catalogs. Having Helga, the compliance assistance bot, is also a very special plus as she can explain terms and provides guidance through the application. We really love and live Compliance Aspekte!
Compliance Aspekte is very user-friendly and customization is easy. We can conduct ISO compliance, and data protection…we can make anything we want in one tool. And this is the only tool with which it is possible. It helps us to keep the data consistent and simplify audits. The Compliance Aspekte tool is better than the existing competitors on the market and at the same time cheaper.
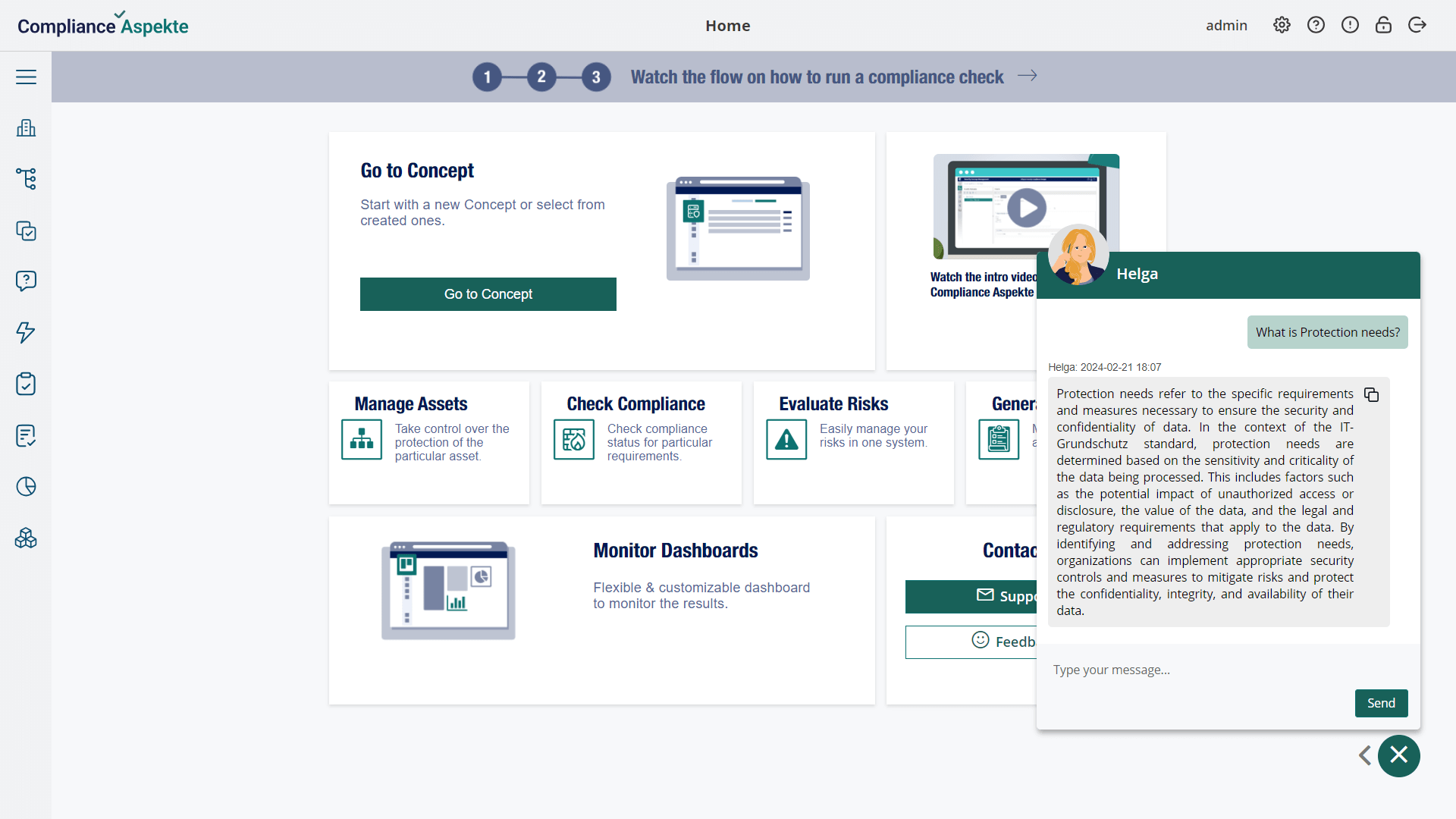
Implement NIS2 measures with
AI assistance
Compliance Aspekte NIS2 tool offers an AI Copilot on demand. This smart assistant is called Helga that is powered by Azure AI GPT technology.
AI Copilot can collect, evaluate, and generate NIS2-related tasks to meet cybersecurity and data protection needs, helping to reduce potential risks effectively.
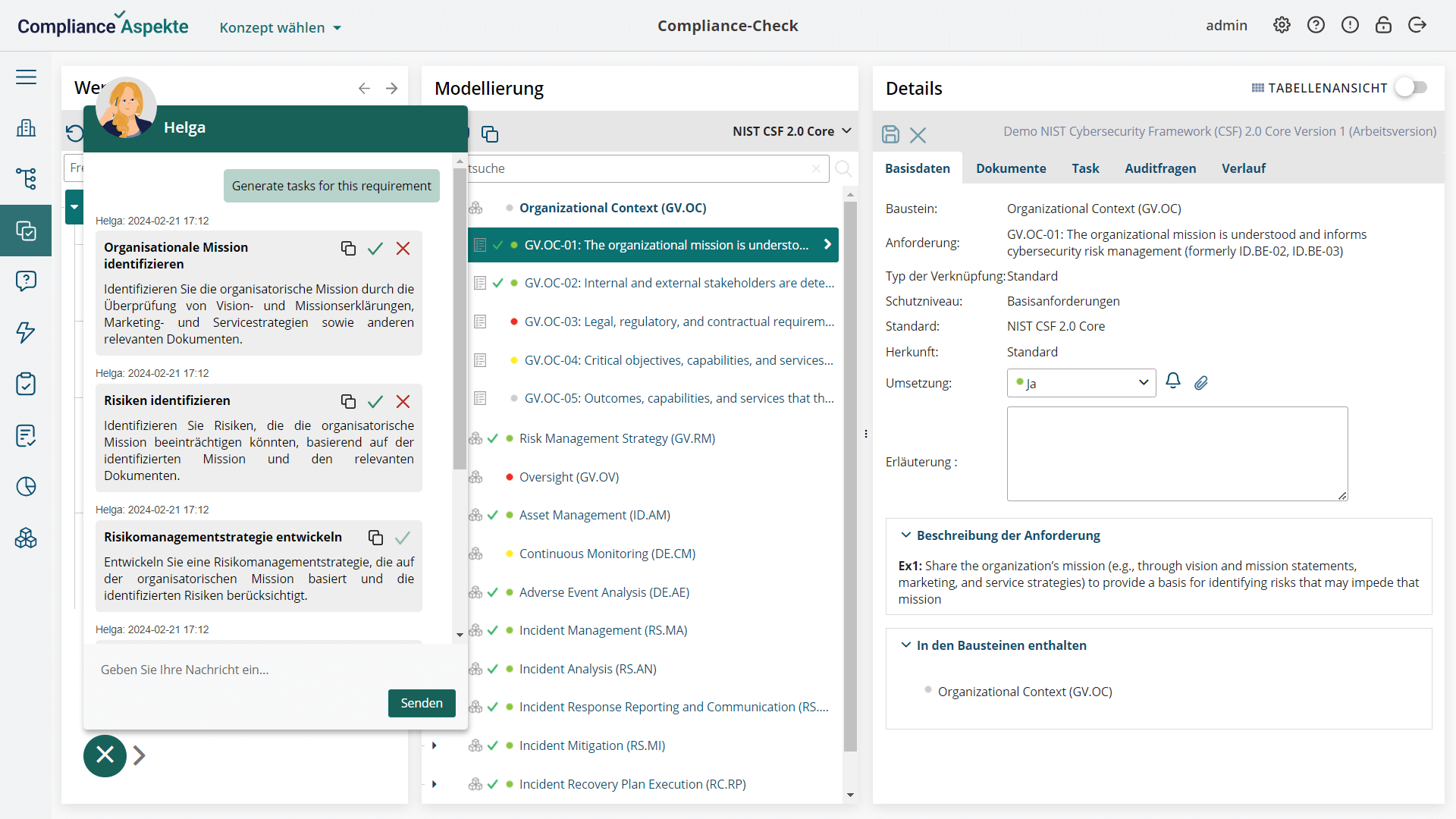
The AI functionality include:
- assigning specific tasks to adhere to NIS2 and related guidelines, ensuring NIS2 compliance;
- offering responses to questions about the NIS2 Directive, requirements, measures and more;
- providing instructions for setting up the Compliance Aspekte NIS2 compliance software;
- responding to specific questions regarding company policies, regulations, and other official documents;
- clarifying how the Compliance Aspekte tool works and its functionality.

What is NIS2?
NIS2, or the Directive on Security of Network and Information Systems 2, is an updated EU regulation aimed at improving cybersecurity across member states. It expands the scope to include more sectors, like public administration and food production and mandates stronger security measures.
NIS2 enhances cooperation between countries, imposes stricter penalties for non-compliance, and requires organizations to report significant cyber incidents within 24 hours. The goal is to boost the resilience and security of essential services and critical infrastructure against growing cyber threats.
NIS2 Basics: What you need to know
When will NIS2 be enforced?
NIS2 was officially adopted by Parliament in November 2022 and came into effect on January 16, 2023. Member States have until October 2024 to incorporate its measures into their national laws.
What are the main requirements of NIS2?
NIS2 mandates that relevant organizations put in place proper cybersecurity practices to keep their systems and networks safe and resilient. These practices include managing risks and vulnerabilities, securing supply chains, responding to incidents, and ensuring secure authentication.
Additionally, the directive outlines the procedures and timing for reporting cyber incidents.
Who is impacted by NIS2?
NIS2 affects all entities operating in the EU that have at least 50 employees or generate over €10 million in revenue and are considered crucial to society.
The directive classifies these entities as either essential, including sectors like energy, healthcare, transport, and water, or important, covering sectors like manufacturing, food, waste management, and postal services.
What are the penalties for noncompliance?
Penalties for noncompliance with NIS2 depend on the entity’s classification. Essential entities can be fined up to €10 million or 2% of their total annual worldwide turnover from the previous fiscal year, whichever is higher.
Important entities can face fines up to €7 million or 1.4% of their total annual worldwide turnover from the previous fiscal year, whichever is higher.
Key requirements of the NIS2 certification
Organizations must adopt measures to manage risks related to the security of networks and information systems.
This includes identifying, assessing, and mitigating risks to ensure protection against cyber threats.
Entities must report significant incidents to the relevant national authorities within a specified timeframe.
This ensures that authorities are aware of incidents that could impact the security of the supply chain and critical infrastructure.
Organizations are required to assess and ensure the security of their supply chains.
This involves evaluating third-party suppliers and service providers for potential security risks.
Entities must establish procedures for managing crises related to cybersecurity incidents.
This includes having a clear plan for communication, coordination, and recovery during and after an incident.
Organizations need to establish governance frameworks that include clearly defined roles and responsibilities for cybersecurity.
Senior management must be accountable for cybersecurity risk management.
Entities are encouraged to cooperate and share information with national authorities and other stakeholders.
This aims to enhance collective security through collaboration and shared threat intelligence.
Organizations must ensure that their staff are trained and aware of cybersecurity risks and best practices.
Regular training and awareness programs are necessary to maintain a high level of cybersecurity readiness.
Entities need to implement measures to ensure the continuity of essential services during and after a cybersecurity incident.
This involves planning for redundancy, backup, and recovery processes.
NIS2 compliance checklist

- Risk management and assessment. Identify, assess, and mitigate cybersecurity risks regularly.
- Incident reporting and response. Establish procedures for detecting, reporting, and responding to significant incidents within the specified timeframe.
- Supply chain and third-party security. Assess and ensure the cybersecurity posture of third-party suppliers and implement measures to secure the supply chain.
- Crisis management and business continuity. Develop, document, and regularly test crisis management and business continuity plans.
- Governance and accountability. Define roles and responsibilities for cybersecurity, ensuring senior management accountability.
- Training and awareness. Conduct regular cybersecurity training and awareness programs for all staff.
- Regular testing and audits. Perform regular penetration testing, vulnerability assessments, and audits to ensure the effectiveness of cybersecurity measures.
The most important innovations of the NIS2

NIS2 expands the number of sectors classified as critical, more than doubling those covered compared to previous regulations.
Violations of NIS2 requirements will face stricter fines, potentially tied to a percentage of the company’s global annual turnover, similar to GDPR fines.
The introduction of managerial responsibility means that executives can be held personally liable for breaches, potentially facing claims for damages from their personal assets.
NIS2 introduces a three-stage reporting obligation for security incidents, ensuring timely reporting even when details are initially unclear.
The reform redefines which sectors are considered critical, moving away from the previous framework under the KRITIS Ordinance and setting new thresholds based on the potential impact on 500,000 people.
Emphasis is placed on efficient incident response, requiring detailed reports on incidents and their management within strict timelines to regulatory authorities.
Benefits of being
compliant
with NIS2
Start for free
- Enhanced cybersecurity posture: Implementing NIS2 requirements improves an organization’s cybersecurity defenses, reducing vulnerabilities and enhancing overall resilience against cyber threats.
- Improved incident response capabilities: Organizations develop robust incident response plans and capabilities, enabling them to detect, respond to, and recover from cybersecurity incidents more effectively and efficiently.
- Regulatory compliance: Meeting NIS2 requirements ensures compliance with EU cybersecurity regulations, avoiding potential penalties and legal consequences associated with non-compliance.
- Protection of critical infrastructure: Ensuring the security of network and information systems protects essential sectors of infrastructure such as energy, transportation, finance, and healthcare from cyber threats and disruptions.
- Access to EU markets: Compliance with NIS2 requirements facilitates access to EU markets as organizations demonstrate adherence to EU cybersecurity standards and regulations.
- Business continuity and resilience: Implementing NIS2 measures, such as business continuity planning and crisis management, ensure the continuity of operations during and after cybersecurity incidents, minimizing disruptions.
Book NIS2 consultation
for your company
FAQ

The NIS2 Directive, short for the Directive on security of network and information systems, is a European Union legislation aimed at enhancing cybersecurity across critical sectors.
It mandates certain cybersecurity measures to ensure robust protection of network and information systems, crucial for maintaining essential services and addressing cyber threats effectively.
NIS2 compliance software refers to tools and solutions designed to help organizations meet the requirements set forth by the NIS2 Directive.
These software solutions often include features for risk management, incident response planning, compliance auditing, and monitoring of cybersecurity measures to ensure adherence to NIS2 standards.
Compliance with NIS2 is crucial for entities because it enhances their cybersecurity posture, reduces vulnerabilities to cyber threats, and ensures the continuity of essential services.
It also helps organizations avoid potential legal and financial consequences associated with non-compliance while fostering trust among stakeholders and improving overall resilience against cyber incidents.
The NIS2 Directive primarily affects operators of essential services (OES) and digital service providers (DSPs) within the European Union. OES includes entities in sectors such as energy, transport, banking, financial market infrastructures, health, drinking water supply, and digital infrastructure. DSPs cover online marketplaces, search engines, and cloud computing services.
The main requirements of the NIS2 Directive include:
- Implementing risk management measures to identify, assess, and mitigate cybersecurity risks.
- Reporting significant cybersecurity incidents to national authorities.
- Ensuring supply chain security by evaluating and mitigating risks from third-party suppliers.
- Establishing crisis management and business continuity plans.
- Implementing technical and organizational measures to protect network and information systems.
- Engaging in cooperation and information sharing with national authorities and other stakeholders.
- Conducting regular testing, auditing, and assessment of cybersecurity measures to ensure effectiveness and compliance.

Effective and easy-to-use IT security management system based on the latest standards and regulations — from planning and establishing the security concept to certification.