Working Remotely: How to Stay Compliant with Basic International Standards in Force Majeure

Today many companies face an unexpected challenge that the outbreak of COVID-19 has brought globally. Most organizations had to switch to teleworking in a few days. Keeping sensitive data safe and the correct handling of personal information are key factors that companies pay special attention to when shifting to the remote mode of work. It is more important than ever to adhere to the most important international standards and to strengthen your information security strategies.
Risks Associated with Remote Work
Remote access to your corporate IT infrastructure is essential to the functioning of your business and the productivity of the working unit. There are external risks that must be mitigated to the best of your ability by designing a secure access policy and implementing compliance controls. The objective of the policy defines and states the rules and requirements for accessing the company’s network to lessen the potential danger of unauthorized use, as it can lead to a loss of the company’s sensitive data.
- Access of third-parties to the device (for example, your family members can use the device);
- Hardcopy material used at the remote worksite can be lost or stolen;
- Loss or theft of the device;
- Unauthorized access to the organization’s systems;
- Interception of data during transmission between the company and the device;
- Blocking of the communication channels and invasion into the organization’s environment
Key Standards to Follow while Facing Force Majeure Challenges
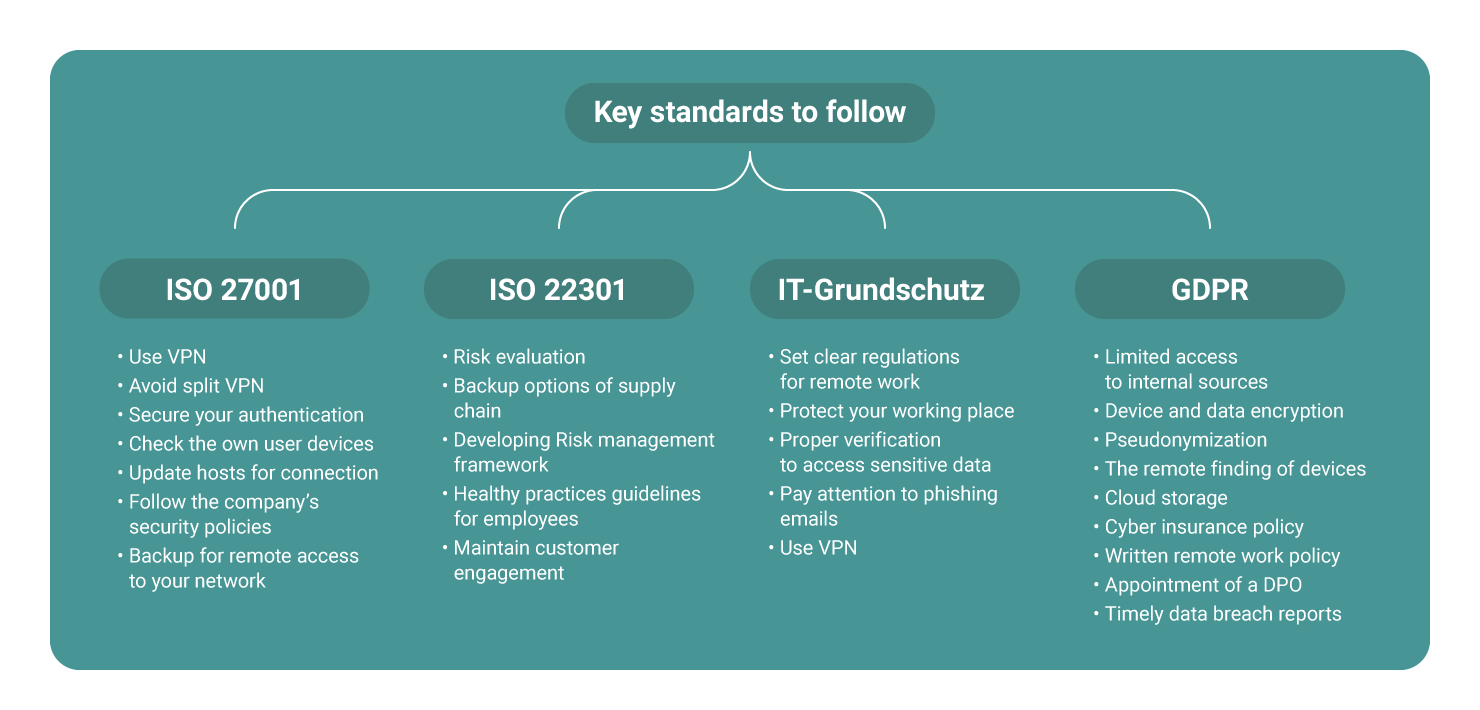
Fulfilling ISO 27001 Requirements for the Remote Access
Remote access to the company’s network should be interpreted as a risk that must have appropriate controls for it required by ISO 27001. Here are the guidelines for defining the rules to eliminate potential exposure due to unauthorized use:
- Secure your remote access and control it strictly with encryption. Use firewalls and secure VPNs, supported by 2FA (2-factor authentication).
- Avoid “split VPN”. Remote users must ensure that their devices (organization-provided or personal) should be connected to no other network, but the company’s network.
- Use other authentication measures and best practices to secure your data transmission. Enhanced security, session restrictions, site-to-site tunneling, and multiple factor authentications will complement the advantages of VPN.
- If users can bring their own devices, the device must meet the requirements of the organization’s hardware, software, and equipment for remote access configuration policy.
- Hosts that are used to connect to the organization’s network must be fully updated with the most up-to-date anti-malware software.
- The remote user should not use access to the corporate network for outside business interests and act illegally. He or she should not violate any of the company’s policies.
- Do not rely on just one provider for remote access to your network. Avoid the so-called “single point of failures“. The keyword here: high availability (HA).
Ensuring ISO 22301 Business Continuity during COVID-19
The COVID-19 outbreak poses several risks to many organizations requiring additional steps to ensure business continuity and risk management. Being prepared for a disaster outbreak makes companies have an effective response to force majeure and successful recovery.
- Evaluate the risk of potential damage. Define which aspects of your business will be affected by pandemic considering demand, supply chains, customers, employees, various events, and what happens in case of a lock-down situation.
- Assess supply risks and check the sources where you can get additional supplies in case your existing chain will be disrupted.
- Design a risk management framework not only in case of a pandemic. Define your essential business functions and project how they will be affected and what could be done to avoid maximum damage.
- Create a guide for employees to encourage healthy practices for your team with regulations and tips on how to protect themselves and their community during the COVID-19 outbreak.
- Think of customer engagement. How will you have to change your interaction with your clients during the outbreak? Consider using additional channels of communication, such as emails, social media, video conferencing, instant messaging etc.
BSI IT-Grundschutz in Force Majeure
Following recommendations of BSI IT-Grundschutz will help you maintain the necessary security levels in the working environment for remote mode based on German requirements.
- Make clear, unambiguous, and binding regulations for IT security and the security of your data in paper form and communicate it in writing to every team member involved.
- Take measures at the home workplaces that can achieve a level of security comparable to that at the office. Lock doors when you leave the workplace, give third parties no chances through visible or even opened windows.
- Provide clear contact points and communication channels that can be verified by the employees.
- Phishing emails can increasingly occur, which will take advantage of the current situation and will try to tap your sensitive data concerning remote access, resetting passwords, etc.
- Use VPNs. Establish access to the company’s internal resources via a secure communication channel.
How to Comply with GDPR During Pandemic
Remote workers may be using public networks to access data and can use their devices in public spaces. When working remotely, it can be more difficult to not only track a data breach but also to identify/track how that breach has occurred.
Nine ways to compliant with GDPR when working remotely:
#1. Control access to internal data
If you don’t want to grant all employees full access, you can create multiple accounts or groups with limited access to files by restricting certain parts.
#2. Encrypt all devices and data
According to article 32 of the GDPR, the company must implement technology and security measures. Data encryption means that only approved users can access a data set. So if a device is lost, no third-party will be able to access the data without the encryption code. Make sure you use encrypted email software, too
#3. Pseudonymization
It is a form of data masking that is highly recommended by the GDPR. It replaces all initial identifying data with artificial identifiers, making it impossible to access personal data without additional information. This “additional information” must be kept separately and secured to ensure non-attribution.
#4. Enable remote finding of devices
Encourage employees to switch on the function of remote finding their devices if it gets lost. Windows, Android or Mac and iOS users can use this option; they will also be able to delete necessary data remotely.
#5. Use cloud storage
Cloud-based storage is a safe option to protect the company’s data from risks. You must manage the data encryption methods used by the cloud storage provider for the end-user. It is recommended to choose an EU based data center if possible or get additional security guarantees from the non-EU provider.
#6. Cyber insurance policy
Create a policy of your organization and have it signed by all your employees. It should cover the following:
- Define a privacy regulator. Usually, the “European Data Protection Authorities (DPAs) are included as privacy regulators.
- In regards to data privacy, the section about violation and breaches pays attention to data storage and processing, as the key concerns of GDPR. Specify how data is stored, managed, and accessed.
- Review the financial limits of your GDPR cyber insurance coverage. GDPR penalty is usually up to 4% of the company’s total revenue.
#7. Written remote work policy
Enhance your GDPR compliance by having a clear and consistent remote work policy. It must cover the following:
- a simplified explanation of the GDPR;
- data security principles;
- rules of copying files and documents;
- step-by-step guideline in case of a data breach;
- responsibilities of the employees and legal obligations.
#8. Appoint a DPO (data protection officer)
A data protection officer is responsible for supervising the company’s data security strategy communication with the authorities in case of a data breach and training employees involved in the data processing. According to GDPR, appointing a DPO is a must if:
- Your company possesses or deals with large-scale sensitive personal data.
- Your company is engaged in the systematic monitoring of people.
- Your company is located in Germany and has over ten employees involved in the processing of personal data.
#9. Report data breach ASAP
Get in touch with the authorities within 72 hours after you discover a data breach, even if you don’t have complete knowledge of the case. Here’s what it’s essential to do:
- Notify a company’s DPO;
- Inform everyone affected by the breach and make sure these persons send you a confirmation they received a message from you;
- Include info about: nature of the data breach, possible consequences, and steps taken to mitigate the risks and the effects of the breach.
Benefiting from a GRC Solution in Force Majeure
Infopulse SCM enables you to quickly access any assets and check if your current status is compliant with the corresponding standard or regulation you’re using in your company. After you have considered physical and digital security, simply note all the changes and adjustments. Just make sure you follow the protection requirements described in the appropriate section.
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
