How to Handle Your Third-party Risk Management

Most businesses today cooperate with third parties; they are using services of the external suppliers, agents, tech vendors, outsourcers, or other service or product providers.
Besides driving cost savings, efficiency, and scalability, cooperation with third parties also involves additional risks for the company to be handled appropriately. The third-party network can be quite vast depending on your industry and the size of your company. Thus it can be challenging to comprehend the outright size and scope of potential risks you are facing. While organizations are striving for more security and reliability, cooperation with external vendors can lead to reputational or regulatory damage because of third-party failures or breaches.
How can you get guarantees and take control of the foreign suppliers to avoid possible risks and create effective third party risk management programs?
Why Third-Party Risk Management Is Important Today
Any cooperation with the external vendors poses the inherent risks of data leakages and security, as your interaction involves sharing some specific data and information with your third parties. With the appearance of new privacy regulations, such as GDPR and the like, companies have shifted their focus to data privacy and more in-depth checks of the suppliers. It refers to the company’s intellectual property, customer data, or other sensitive information.
The frequency and scale of vendor use are changing, so do the regulatory focus on how organizations manage third parties. Most companies today are beginning to pay more attention to specifically developed third party risk management policies to ensure their external suppliers are reliable and secure.
Third-party risk management (TPRM) is the strategy that involves control and analysis of potential risks associated with third-party service providers. It involves reviewing, monitoring, and managing communication over the entire third-party lifecycle and aims to reduce the likelihood of data breaches, operational failures, and to meet regulatory requirements.
Creating a Third-Party Risk Management Framework
Companies usually address third-party risk management using a few in-house experts for monitoring specific risks. The first thing to do when approaching the TPRM is to identify all the third parties they are dealing with and understand the associated risks. Usually, companies concentrate their efforts on those that may pose the highest risk. It’s more of a standard approach.
Then they create a questionnaire for third parties and are supposed to collect potential risks based on the answers they get. Once all the risks are identified, they should be handled through a clear step-by-step policy that defines which risks can be accepted and how they should be properly managed.
What usually holds organizations back from fully enforcing third party management programs are technology limitations. This results in tons of spreadsheets and documents that even global enterprises try to use for third party risk management.
A holistic approach to risk management involves more in-depth analysis and a defined process for assessing third-party risks. It consists of the creation of automated frameworks that are more manageable and efficient in use.
Getting a Third-Party Risk Management Guidance
Getting access to overall risk exposure and managing it enterprise-wide is what many companies are missing at the moment. Infopulse SCM can assist you in enhancing your TPRM programs or functions, systems, and technologies, and manage third-party risks.
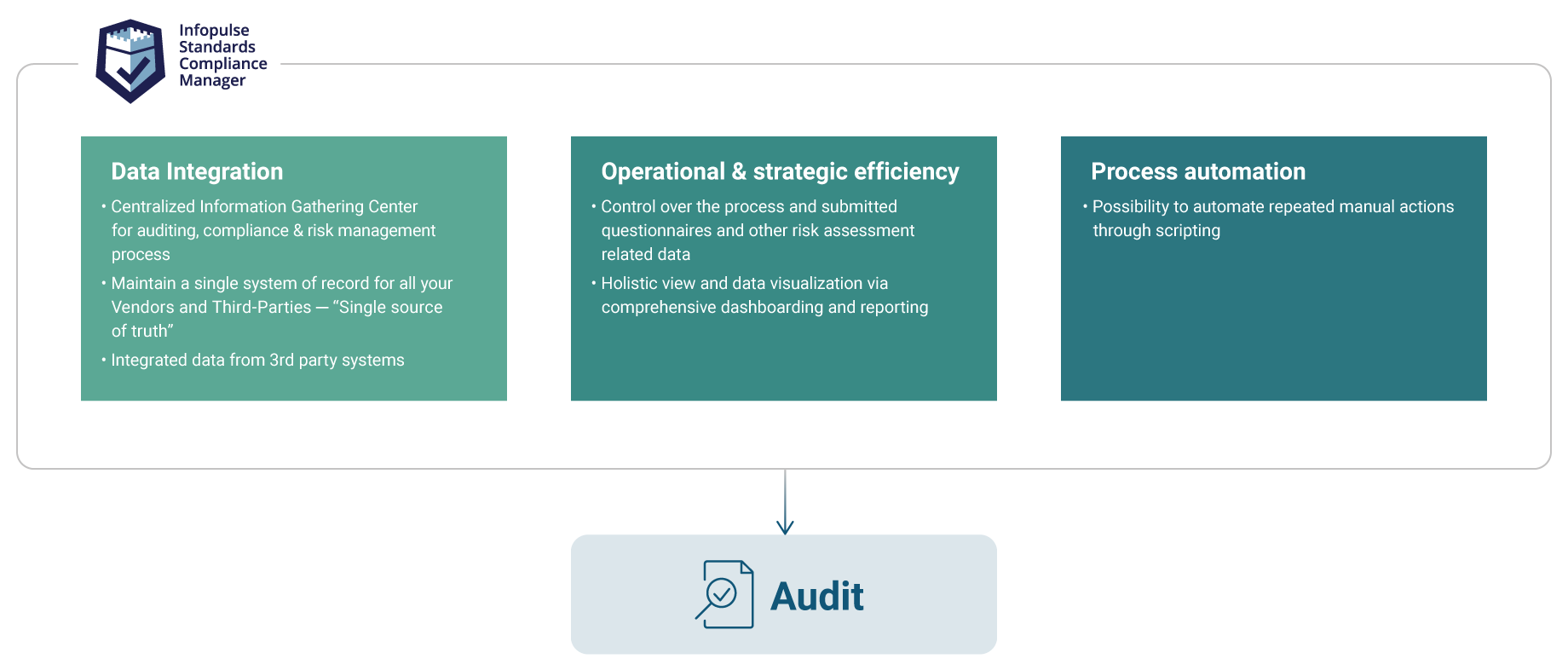
Our solution allows you to build a third-party risk management program, simplifying all processes and improving existing ones. With Infopulse SCM, you will be able to create from scratch or scale your current TPRM program without the necessity for additional employees or resources.
Infopulse SCM risk management lifecycle consists of:
- Risk Identification
- Risk Analysis
- Risk Treatment
- Risk Monitoring.
In the risk analysis tab with all target objects requiring risk analysis, you can select an asset to see the list of related threats and their risk matrix. Each threat can be analyzed. You will determine the probability of its occurrence and the potential damage it may cause.
What Infopulse SCM Can Do for You
Our GRC solution provides you with the step-by-step guide for building a detailed compliance risk program, including both existing and potential risks your organization may face and offering steps to mitigate those risks.
Infopulse SCM enables you to go through the complete risk analysis cycle:
- Create, group, sort, filter & edit Questions for questionnaire and match them with safeguards.
- Reuse Questions for different objects and concepts.
- Link Questions with Requirements/Modules/Assets.
- Get approval from the C-executives or senior managers.
- Assign and set due dates.
- Publish and send to the 3rd party for the assessment.
- Monitor assessment activities and schedule them.
- Get intermediate status reports.
- Export of findings for further Reporting (Excel, CSV) + Data Grid.
- Hold discussions with third-party assessors.
- Review assessment reports.
- Prioritize the identified risks in the system depending on your risk strategy.
- Develop remediable plans.
Infopulse SCM provides the technology and process necessary to fully understand supplier-related risks, help you fix ineffective controls, and better protect your company from potential security hazards. Start using this GRC solution for your third-party risk management-as-a-service today.
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
