Assistance in Achieving Security Excellence
The scale of malware deployments, cyber-attacks, and frauds is overwhelming. It gives the impression that cybercriminals are always one step ahead of the technologies. It is often true. Many of them are at the peak of the technologies. That is enough for their success because many organizations are far from following common security practices.
How can you be confident in your systems and information safety? To find out the answer let us take a closer look at security most common issues.
Security Support in Compliance
Managing compliance with multiple standards manually is costly, resource-consuming, and low efficient.
Modern software solutions enable consolidating all compliance processes in one control center eliminating silos, overlapping, and gaps. They provide a comprehensive assessment of both security status and associated risks. The most advanced platforms like Compliance Aspekte offer dozens of features to streamline and simplify your compliance processes.
Imagine you have received all advice and guidance from the vendor, and your compliance solution is finally in place. What can be your next move in enhancing the protection of your systems? Considering the complexity of security requirements and thousands of controls coming from security standards, using automated solutions to their full capacity requires a lot of in-house security expertise. This leads us to the next stage of improving your protection quality.
You have an opportunity to receive professional advice on any security issue on the go. The Infopulse GmbH security experts will carefully guide you through the SCM implementation stage. They show you how to use product features in the best way. Whatever it may be, compiling an inventory, risk analysis, or system modeling – you will get firsthand instructions based on the best security practices.
3600 Protection with Security Services
Cybersecurity is a complex of technologies and methodologies. Even the most advanced automated tools, however efficient and convenient, do only part of the job. They give you numbers, alerts, assessments, recommendations, etc. It is more about a view on protection status than the protection itself.
That is why, besides the SCM and security support, Infopulse GmbH offers a full range of Security Services. Created by security experts, they provide a holistic approach to cover all aspects of information security.
Security Assessment
Security Assessment services help our clients identify and analyze all possible security threats and organizational weaknesses. Based on industry best practices and customer requirements, our information security experts provide an individual assessment of the organization’s security vulnerabilities and risks.
Security Assessment performance is in line with the requirements of ISO 27000 series, NIST SP 800 series, ISF SoGP, BSI IT-Grundschutz, and GDPR.
Penetration Testing
Penetration testing gives a true picture of your system’s protection level. What could be more convincing than the simulation of a real cyber attack?
Penetration testing goes in line with the requirements of NIST SP 800-115, PTES, OWASP, EC-Council. It helps to assess the security of your information systems in several dimensions: networks, applications, personnel adherence, and embedded devices.
Continuous Cyber Reconnaissance
You cannot imagine how much sensitive information companies carelessly spill around in open sources. Cybercriminals can use it against your organization to get insights into potential vulnerabilities.
Running open-source intelligence reveals this harmful information and the related risks you might expose yourself to. Our security experts can further leverage the found vulnerabilities during a penetration test, red team exercise, and other specific techniques.
Cloud Protection
The fast adoption of cloud technologies along with massive virtualization exposes their users to specific threats. Our experts ensure the full protection of your data, infrastructure or applications in the cloud. We provide expert advice and all cloud-related services to enable and protect your business.
- Identity and access control provide another layer of protection at the user level.
- Information protection ensures that only authorized people get access to communications and documents.
- Threat protection fights advanced threats and provides tools for fast recovery when attacked.
- Security management arms you with tools to control all compliance and security processes.
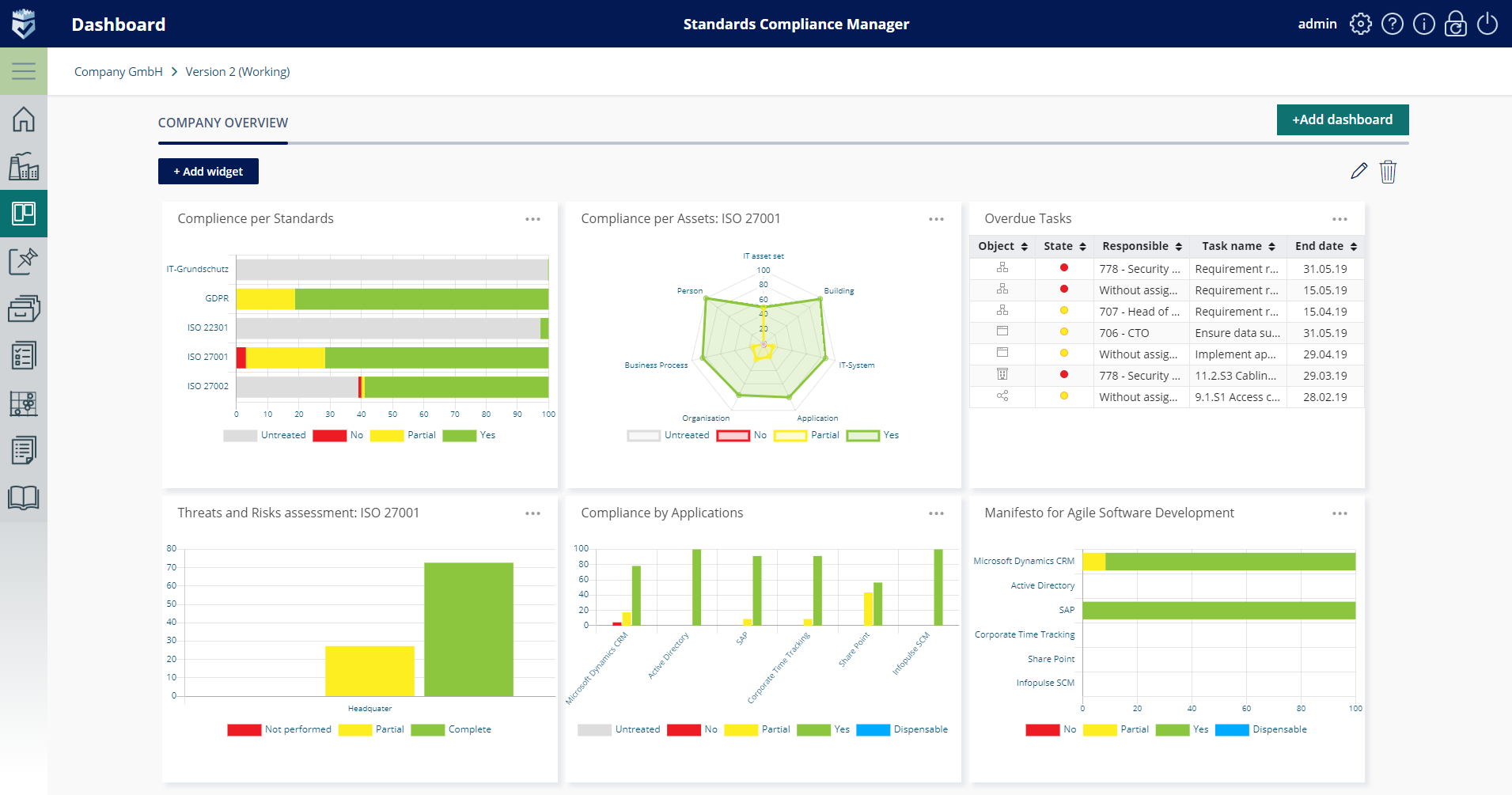
IT Infrastructure Protection
This service provides end-to-end protection of your on-premise, cloud, or hybrid environment, and data stores. The Infopulse GmbH certified experts with real-world hands-on experience will assist you in protecting your IT infrastructure from cyber threats.
Monitoring your network perimeter and network servers’ configuration we create your Risk Treatment Plan to mitigate security risks.
Security Operations Center (SOC)
Compliance Aspekte provides both SOC-as-a-Service and SOC-as-a-Solution depending on your needs. 24/7 operating SOC allows instant identifying cyber attacks and taking preventive actions. That means less damage and faster recovery.
You will get real-time control over security events and the assistance of an experienced Security Incident Response Team.
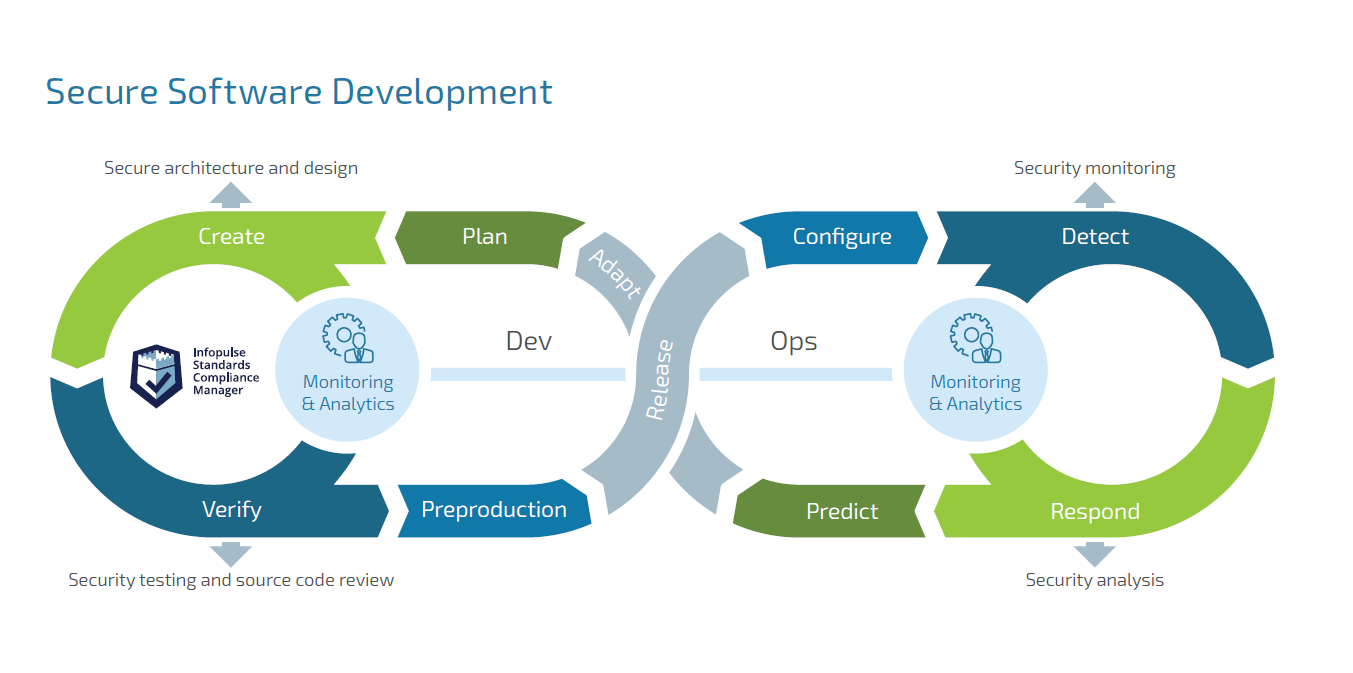
Secure Software Development
It is about a specific approach to software development operations based on the idea of “security by design”. The SCM platform enables developers and security professionals to organize the development process around security best practices. It integrates related requirements of several standards. In particular, these are ISO 27K series, IT Grundschutz, ASPICE®.
Our specialists will guide you through the Secure Software Development process. The service includes threat modeling and risk analysis, security architecture design, source code review, security testing, etc. And we use worldwide standards and proven best practices, such as ISO 15408 & CC Protection profiles, OWASP, NIST SP 800-64, NIST SP 800-115, and CIS recommendations.
As a Final Remark
Security knowledge base and techniques keep evolving along with the emerging technologies of the data-driven world. There is no final and utmost protection for all times, unless you have nothing to protect. Millions of cyber-attacks worldwide daily challenge security of the information systems. It is a battlefield where no one can feel safe for a long while.
Anyway, before considering all the opportunities, it makes sense to explore your vulnerability landscape. The best option for it would be penetration testing. It will clearly show where you stand in terms of security and what service you might need.
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
