(archive)
Aligning Business Operation and Security

Conflict of Priorities
The purpose of IT department has always been the same – to grow business productivity through technology. The number one priority for IT is facilitating business operations and providing continuity. Their priorities mostly come from the business processes they support.
On the other hand, the business operation teams strive for agile delivery. Their top priority is getting business operation processes moving as fast as possible, even if it strains IT resources beyond the extreme.
Security department balances in the middle trying to fulfill its core mission: to ensure business security and maintain compliance.
Business operation supported by the IT team strives to deliver as fast as possible. They all often view security as an inhibitor. Why? Because it takes extra time to check the processes, products and supporting infrastructure against vulnerabilities and known threats, verify that app configurations meet requirements, and that adopted security policies and standards are complied with.
By establishing policies, and identifying threats and vulnerabilities security urges IT to follow baseline configurations, timely apply patches, and run updates. However, taking into account its limited resources, IT gives security initiatives lower priority than the needs of current business operations for agile delivery.
Mapping Security Priorities onto Business Operations
When no security incidents happen for a long time, the security unit is pushed into the shadow and underestimated. However, when adverse security event happens, they are first to blame. That explains why the security department should place the focus on tight collaboration with the business leadership to deliver ideas that resonate well with them.

For many business leaders, a security breach is a mere possibility. Their major expectation from the security team lies in providing business continuity. Given that, the security team should present:
- Security metrics relevant to business development
- Security risks and associated damages
- Industry best practice benchmarks
- Opportunities for the business goals: for instance, a reduced cost due to standardized configurations, which meet security compliance requirements
The challenge is to make business leaders understand and agree on the acceptable level of risk. Then, security requirements associated with the accepted level of risk must be fixed in the roadmap. IT unit will have to follow the adopted initiatives and focus on mitigating the risk while working on delivery. Thus, the security department changes its position from an alleged inhibitor to a partner of business development and IT units.
Focusing on Business Efficiency and Continuity
With the growing security risks, technology organizations opt to use modern security platforms to improve their operations and efficiency. Having effective and intelligent Information Security Management Systems (ISMS) in place is critical. Investing in security software solutions is as important as it is in the other components of the security system.
Driving security through the mesh of business daily operations, modern security solutions improve an organization’s efficiency and business continuity in several dimensions:
Mitigating Organizational Risk
Businesses housing thousands of employees and petabytes of sensitive or mission-critical information residing inside a giant infrastructure face the whole gamut of security challenges. Given the growing amount of data stored and processed, organizations must be aware of activities taking place inside and outside their offices, so that they could quickly recognize the unfolding adverse event and take appropriate response action.
Meeting Security Standards Compliance
Security standards like ISO/27K Series are the core of any information security system, but implementing and maintaining compliance with them is a longtime pain for many organizations. Automation is the keyword, but most of existing compliance management solutions either have too limited functionality or are critically tooled for a specific application.
All-encompassing solutions, such as Compliance Aspekte, integrating regulatory and industry-specific standards, create a clear-cut and easy path to get control over all compliance-related processes via one center. By streamlining and leveraging all security-related processes on a global scale, such tools enable reducing costs, mitigating risks, and meeting compliance requirements.
Recent stats about security breaches leave no illusion about the consequences of security compliance negligence, in terms of both damages and penalties. Taking into account the severity of breach implications, your best bet is to have more than just a primitive compliance management solution. It has to be a holistic platform enabling prompt and adequate responsive action based on real-time assessment of security status, and associated risks and providing live instruction on the required actions.
Overcoming Logistical Bottlenecks
A security event is a challenge for any business, but it is more so for companies with decentralized management often met in law, consulting, and technology businesses. Management decentralization with a focus on projects/cases rather than on functional areas hinders the fast delivery of emergency response commands through the chain.
Therefore, highly decentralized organizations must take into account their own specific non-hierarchical structure in the security event management and disaster recovery documentation. It refers to your training programs too. It is important to focus on case studies incorporating best practices of crisis management in your industry. This is where modular, highly flexible solutions like Compliance Aspekte are indispensable. It enables you to set up, configure or customize any functional component exactly to the needs of your organization. Moreover, you can add your own customer-specific standards, policies, or procedures to the system.
Improving Business Operation Efficiency
Consolidation of all security-related processes in one center contributes to streamlining business operations and improving their efficiency, especially in organizations with a large physical footprint. Using industry-leading solutions designed to maintain security operations and compliances, organizations can significantly reduce both response time and the number of false alarms.
Since business continuity and operational efficiency are the organization’s top priorities, a proper security platform becomes an invaluable solution for risk mitigation, resolving logistical bottlenecks, and cutting costs. Based on real-time security status monitoring and regular risk assessment the system prompts the best sequence of remedial actions.
Cybersecurity is no Longer a One-field Battle
Massive digitalization and hyper-connectivity of the modern economy became a reality. Governments, businesses, financial institutions, educational establishments, public services – every industry, every facet of society are undergoing a fundamental digital transformation in the era of online search aggregators, booking portals, payment ecosystems, chatbots, robotics, and artificial intelligence.
The downside of technology advancement is the exponential growth of cyber threats to organizations and individuals worldwide. While individuals are exposed to a high risk of privacy breaches, identity theft, and financial fraud, businesses can experience a disastrous impact from targeted cyber-attacks. Hefty regulatory penalties, plummeting stock prices, production downtime, disappointed customers, lawsuits, and other consequences can be catastrophic.
Organizations have to contend with the new challenges of employing different security strategies before they become aware that their systems and networks have been compromised. The general challenge is that employing more lines of defense is resource-consuming and demands highly qualified security personnel. Many understaffed companies go the reactive way taking action only after an eventual security event has occurred.
The most crucial mistake is to relegate security functions to a single department, whether IT or Security. Today, everyone in the organization must consciously share responsibility for corporate security. Business leaders must accept this idea in the first place, and systemically deliver it down to the company’s personnel.
The all-encompassing nature of modern cyber threats dictates new rules for creating secure business environments. Given that in most cases end users prove to be the weakest link in the security chain, it is obvious that building a corporate security system must begin with an individual, who is the first line of defense against cyber attackers.
Read moreHow vulnerable our Systems are?

It is about organizational and technical security aspects.
Organizational aspect involves security practices, processes, policies, and standards implemented in all organization processes. It also includes the security hygiene and behavior of every employee within the organization. This is the primary level of protection.
Technical aspect relates purely to technology. Putting it very simply: bugs in the code, insecure environments, low-protected networks, poor password management, and… hundreds and hundreds of unsafe software development habits that finally land in your organization.
This article relates to the information security of the entire organization including people, processes, and technical vulnerabilities of corporate infrastructure, websites, or user applications.
Vulnerabilities in People
We can look at Vulnerability as a loophole in the system allowing an attacker to cause damage to your assets. In most cases, humans are the weakest link in the chain. The ever-growing number of social engineering and scamming tricks artfully targeted at human foibles, desires, or fears practically meet no resistance.
So the assessment of your organization’s vulnerabilities and associated risks always includes the human factor. Let see a little bit statistic on this.
The Scam Watch Radar of the Australian Competition and Consumer Commission (ACCC) provides overwhelming stats about the scams pulled on individuals daily nationwide. The fact worth mentioning is that the prevailing delivery methods are phone and email.
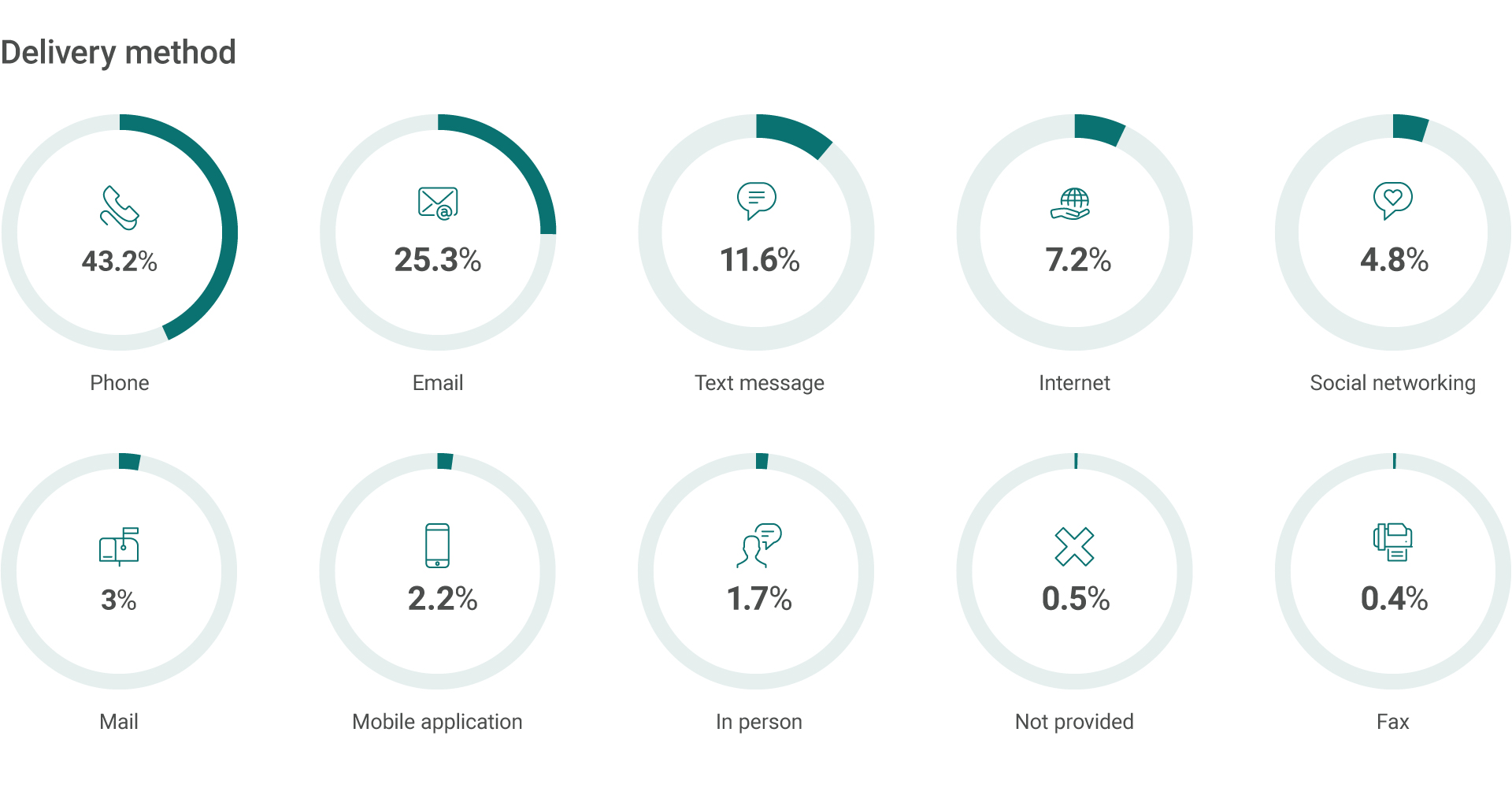
We are of a strong opinion that security in an organization starts with its employees. Today, information security is no longer a business of IT departments only. It is everyone’s concern, from top to bottom. The highest and the lowest rank employees are the Target No. One. The former are the most lucrative catch, while the latter are the easiest to get through.
Inviting all employees to an annual CISO’s cybersecurity report meeting and getting them regularly sign new policies do not work. It is about grow a mature security culture. It is about getting everyone truly engaged into a new paradigm of the Digital Age: cyber protection of your environment begins with you personally.
This can be achieved through teaching the employees to be responsible for the common security and cultivate correspondent skills. Teach them to stay alert and follow secure practices continuously not because it is a requirement from authority. Because this is the only way to maintain the organization’s security.
To add one more detail that is important: invite experts to test and train your employees to resist the effective methods of social engineering.
Vulnerabilities in Processes
National and international standards related to information security ISO 27K series, IT-Grundschutz, GDPR, etc., provide detailed guidance on building secure ecosystems. However, implementing and maintaining compliance with the standards is a challenging task for any organization regardless of its size.
First, it is due to complexity and versatility of requirements. To take off from the scratch translates into significant cost and effort. On the early stage, expert advice is an invaluable contributor to put things right from the start.
Failing to follow the best security practices creates much risk that vulnerabilities in the inappropriately established processes would pile up in a blink of the eye.
The highly recommended approach includes using automated solutions. They have a range of obvious benefits:
- Create a clear path to achieving your security objectives
- Eliminate silos, double-entries and responsibility overlapping
- Reduce cost, and free resources
- Put you in the control of every detail of organization’s security and compliance
- Simplify compliance management
- Minimize the possibility of human error
Besides, compliance platforms like Compliance Aspekte provide a variety of convenient features for risk assessments, real-time control, reporting, auditing and so on.
Vulnerabilities in Infrastructure
Certain compliance activities are also aimed at security of infrastructure. They include having the most recent versions of operating systems, all applications timely patched and updated, proper access and password management procedures in place, etc. These organizational measures are surely not enough.
International organizations like OWASP unite the efforts and expertise of security professionals worldwide around the web applications security risks. They provide guidance, tools, cheat sheets, videos and extensive conferences to anyone interested in improving application security.
The list of app vulnerabilities is huge. Here are a few examples:
- SQL, NoSQL, OS, and LDAP injection
- Cross Site Scripting (XSS)
- XML External Entities (XXE)
However, checking your software and hardware for known vulnerabilities is another challenge on the way to a secure system. This task is for highly qualified security professionals with hands-on experience in dependency analysis and penetration testing, have correspondent tools and relevant proved techniques. If in your organization there are no specialists of this level, you can outsource this service from reputable security providers.
Dedicated Information Security Services
Compliance Aspekte helps its customers to identify all the potential threats and existing vulnerabilities in their system.
Our most often demanded services include:
- Penetration Testing, including Social engineering
- Source Code Analysis
- Assistance in Security Audit Preparation
- Risk Assessment
The Compliance Aspekte security experts detect and identify security flaws, threats and related risks providing you with recommendations on the improvement embedded into a complete action plan.
Contact the Compliance Aspekte security experts to find out how firm your system stands on the ground. Individual objectives, holistic approach, and 100% reliable result.
Read moreWelcome to NetWork’19 Event!


This year, NetWork’19 will be a two-day forum on Service-, Telecom- and IT Infrastructure management technologies. Covering various aspects of cloud transformation, digital evolution, and infrastructure automation, the event will be of special interest for IT, Telecom and Information Security leaders and professionals.
Visit NetWork’19 to communicate to world-class technical experts, entrepreneurs, and decision makers within a variety of discussion panels, live workshops, and presentations of the newest software solutions from FNT partners.
Meet us during NetWork’19 event on March 13-14, 2019 in Aalen, Germany
Read moreInfopulse Standards Compliance manager 4.0 Released

- Onboarding page – first view after user’s logon containing text and video instruction on app’s workflow for beginners;
- Home page – app’s main view with improved UI containing menus and controls to navigate SCM
- Dashboards – unlimited in number customizable visualized dashboards to monitor and control performance;
- Adapt Profile Object – specific functionality for editing or customizing Profile Objects
SCM is an integrated tool designed to implement and manage compliances with any requirements, standards, policies, and procedures including a variety of customizable features to run audits, assess and manage risks, monitor compliance status, prepare to certifications and much more.
The Infopulse SCM 4.0 release contains improved as well as newly added features aimed to enhance user experience. The major features to appear in this release:
Onboarding page
The Onboarding page is the first thing user would see when logged in to the application. The basic idea of adding the Onboarding page is to make user familiar with general application workflow and help them learn the basic concepts and controls fast. This primary view offers a simple tutorial presenting several steps with text explanations and a video guide. Advanced users can skip displaying this beginner view by checking “Do not show me the flow again.” If needed, one can open this page via the link on the app’s Home page.
Home page
Home page is a basic view that user sees after the Onboarding page, or it becomes the first view if the user opts to skip Onboarding page. One can promptly open Home page from any location via Main menu. It provides a convenient start point to navigate all working areas including Onboarding page and Contact Us form.
Dashboards
Variable information dashboards enable tracking data from multiple sources within the specified Security concept in one place. This extremely flexible feature is a perfect visualizing tool for real-time performance analysis and monitoring. The dashboards display key indicators in the form of data sheets, charts, and animated gauges providing a clear view of compliance status and performance by specified criteria or concerning particular processes. The feature enables creating an unlimited number of individual dashboards equipped with a selection of widgets to meet the specific needs of an organization or user.
Adapt Profile Object feature
This functionality allows customization of Profile Objects, such as Modules, Requirements, Safeguards, and Threats. Profile Object adaptation serves to change or amend Profile Object name, Description/Implementation notes, and create additional links with associated Profile Objects. On the other hand, it allows re-setting Profile Objects to their default values.
Other smaller improvements of the existing functionality and features relate to enhancing user experience. Through tight collaboration with the product practical users, Infopulse keeps the focus of SCM further development on the most relevant needs.
This website, fully dedicated to SCM and its development, is another evidence of Infopulse’s commitment to enhancing its customers’ experience. See detailed information on the product in all its aspects: product features, editions and pricing, advantages for specific industries, integrated standards, partnership programs, news, technical support and a lot more!
Request a demo of Infopulse SCM or upgrade to 4.0 version.
Read moreInfopulse to Present Standards Compliance Manager 3.0 at it-sa 2018

Keeping up its front-runner ambition, Infopulse again is meeting you at it-sa 2018 – a number one IT Security Trade Fair in Europe. The first-class security gurus, experts, and opinion makers get together at Nuremberg Exhibition Center, Germany on October 9-11, 2018 to address the most burning security issues of today, discuss trends and share the latest achievements in the field.
This one of the most outstanding IT security events worldwide for C-level managers and IT security officers houses industry-changing conferences, workshops, forums, and technology expo with about 700 exhibitors.
Any Standard – Any Process: The Standards Compliance Manager 3.0 to Be Exhibited at it-sa 2018
With a profound longtime expertise in security solutions and services, Infopulse is proud to present its next-generation development – the Standards Compliance Manager (SCM).
This tool, with governance, risk and compliance management all in one solution, allows businesses making fast and efficient assessment of their current business, infrastructure and data protection status, as well as its compliance with security requirements of any established standards, policies or procedures. SCM provides for all stages of security management from conceiving a security concept and planning to certification and maintenance.
BSI IT-Grundschutz and GDPR were inbuilt in the tool by design as the fundamental guiding models, but feedback received from tight collaboration with our customers prompted us to add also ISO 27001 and ISO 22301 standards to the functionality of the product. Special highlights are the mechanism to create, upload and use your own customer-specific standards and the possibility to import data from any existing CMDB. Due to its modular structure, SCM offers extreme flexibility to adjust any of its components exactly to your custom needs. Moreover, thanks to the intuitive web-based interface it is easy to use and always available. SCM becomes your invaluable tool in building and maintaining the compliance of your entire business.
In the expo premises, Infopulse will run live SCM demo sessions to showcase its key features, extended capabilities and major benefits for your entire information security.
You will also be able to participate in our live hacking demo and get insights about how hackers act and attack.
Last but not least, for the early birds, we will speak about DO’s and DONT’s in GDPR at the management forum (hall 10), at 10 o’clock, 9th of October.
Join us at it-sa 2018
Try SCM live and have a chat with our product Profs! Visit us at booth no. 314, hall 10.1 on Oct. 9-11, 2018!
For any further information or booking a meeting, please contact:
Daniel-Steffen Schreiner, Business Development
Phone: +49 7971 919 01 70
Mobile: +49 (0) 152 092 974 27
Looking forward to meeting you at it-sa 2018!
Read moreEffective and easy-to-use IT security management system based on the latest standards and regulations — from planning and establishing the security concept to certification.
