Security Risk Analysis: A Step-By-Step Guide

Tech advancements and the current cyber environment continuously push organizations to enact measures to satisfy security regulations. Moreover, they must go beyond the bare minimum to strengthen their ISMS to keep them comprehensive, scalable, and resilient. That’s why security risk analysis has become a paramount requirement of many information security standards and regulations.
Contents:
- What is Risk Management?
- Difference Between Risk Assessment & Analysis
- What is Risk Analysis?
- Types of Risk Analysis
- Five Risk Analysis Steps According to BSI IT-Grundschutz
What is Risk Management?
Risk management identifies, analyzes, and manages threat factors in a business’s lifecycle and day-to-day operations. Such management aims to prevent or minimize future outcomes by acting proactively rather than reactively. As a result, effective risk management reduces the likelihood that a risk will occur again as well as decreases its potential negative impact on business.
Risk management is an integral part of Information security management. The synergy of both creates information security risk management or ISRM — the process of identifying, evaluating, and treating risks related to the organization’s information and the use of information technology.
ISRM can be successfully enforced with a practical approach, including risk analysis and modern techniques. ISO 27001, ISO 27005, ISO 31000, and BSI IT-Grundschutz are international standards that specify risk approaches for creating and following effective risk analysis models.
Difference Between Risk Assessment & Analysis
There is confusion between these terms which is quite easy to clear up. The last one is a broad term that includes assessment and analysis. According to ISO 31000, risk assessment is the overall process of threat identification, analysis, and evaluation, while risk analysis is a crucial component of the assessment process.
What is Risk Analysis?
In IT-Grundschutz, the definition of risk analysis refers to the complete process of determining (identifying, assessing, and evaluating) and treating threats. While in the ISO 31000 and ISO 27005 standards, the analysis only refers to a single step in the risk assessment.
Types of Risk Analysis
The two primary risk analysis and risk assessment methods are qualitative and quantitative. Using predefined ranking scales, the qualitative approach estimates the likelihood of a risk occurring based on subjective qualities and the effect it could have on a company. As each threat is identified, it is ranked according to its priority — low, medium, or high.
Typical risk analysis examples of the qualitative method are:
- Risk matrix
- Cause and effect diagrams
- SWOT analysis
Using the quantitative method, an adverse event will be assigned a specific financial amount representing the potential cost to an organization and the likelihood that it will occur in a given year.
Five Risk Analysis Steps According to BSI IT-Grundschutz
IT-Grundschutz standard 200-3 provides a more straightforward methodology than traditional methods for qualitative analysis. Here are the basic steps in the risk analysis according to BSI Standard 200-2 performed with the Compliance Aspekte tool.
1. Modeling: Preliminary Work
The task of the modeling process is to identify which basic and standard security requirements have already been met and identify the gaps. In this step, you will create a list of target objects for which a risk analysis should be conducted.
During this phase, you will evaluate the protection requirements of your assets and assign the levels “Normal,” “High,” and “Very high.”
Define if there are corresponding IT-Grundschutz modules to each target object and how they will be applied.
The modeling process can be automated with the Compliance Aspekte solution:
- Automatic assignment of IT-Grundschutz modules recommended requirements and controls;
- Monitoring of the implementation status of defined controls, requirements, and assets;
- Bulk-editing of data, e.g., changing the realization status of requirements and controls for multiple assets;
- Assignment of people responsible for task realization and controlling;
- Data visualization from different perspectives uses various table view options (e.g., grouping by IT-Systems with not implemented data backup requirements)
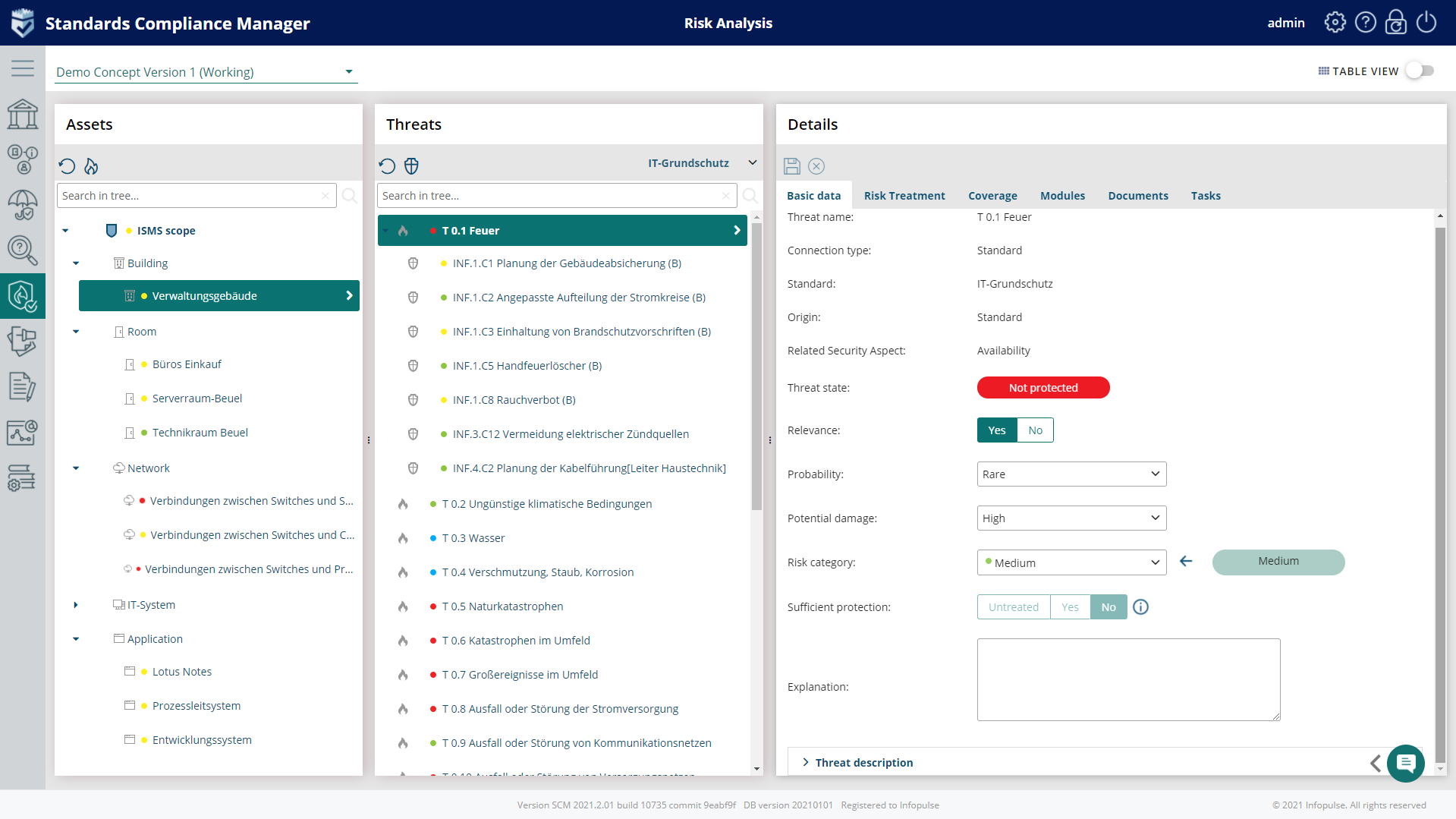
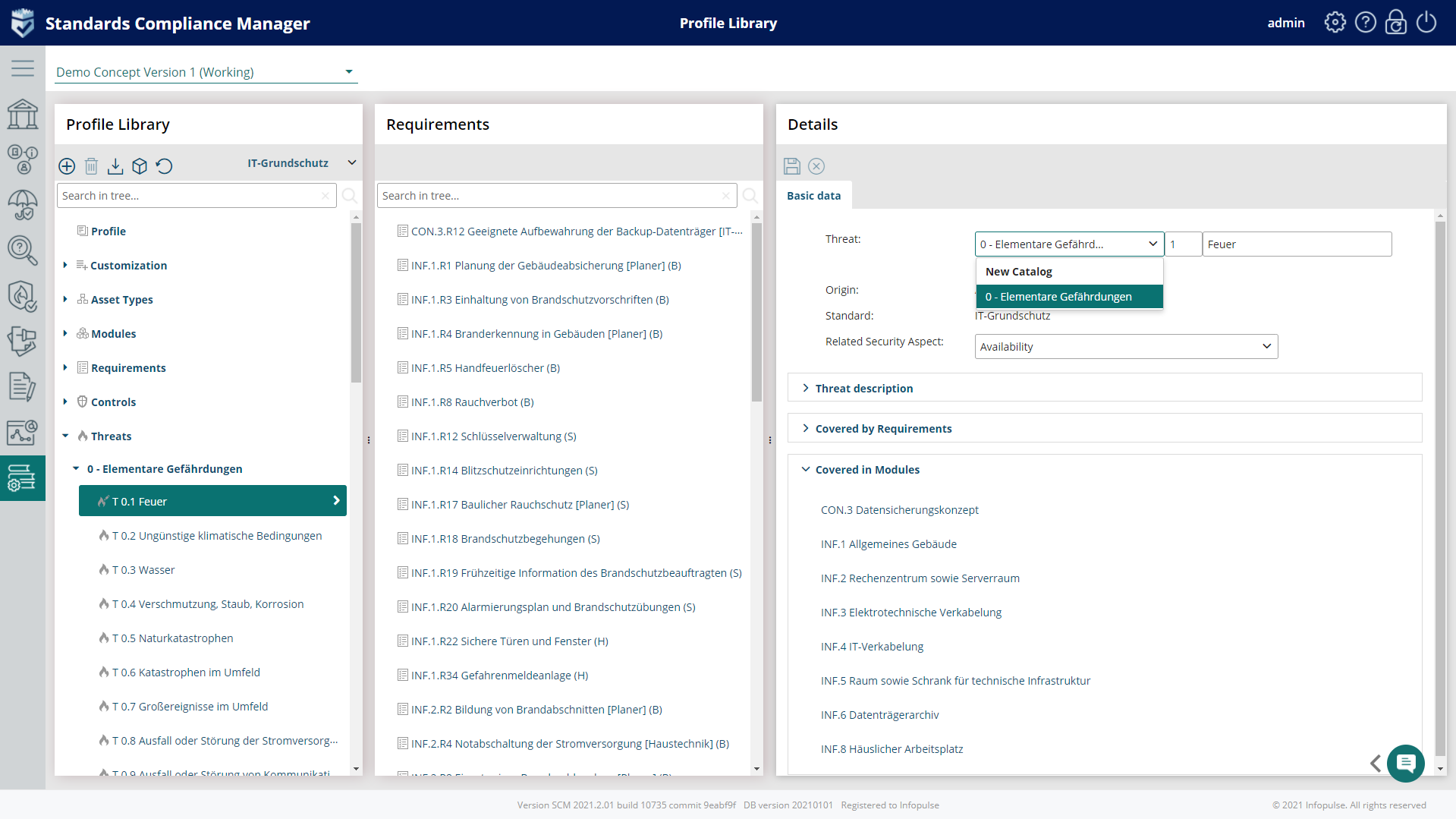
2. Threat Analysis
Each IT-Grundschutz module contains a list of typical threats classified in threat catalogs: 47 elementary threats are listed in the IT- Grundschutz Compendium, which includes malware, data loss, disclosure and the loss of integrity of sensitive information, manipulation with software & hardware, manipulation of information, unauthorized access to IT systems, software vulnerabilities or errors, misuse of personal information, and many others.
“Cybersecurity control failures was listed as the top emerging risk in the first quarter of 2021 in a global poll of 165 senior executives across function and geography – Gartner.”
The Compliance Aspekte risk analysis tool provides a detailed description of each threat contained in a module:
- Adaptable catalog of threats specific to individual organizations available in the Profile Library;
- Set of pre-defined catalog templates, e.g., threat Catalog from IT-Grundschutz Compendium;
- Automated risk analysis for assets with very high and high protection requirements;
- Identification of threats and vulnerabilities and mapping to the related assets or processes;
- Available risk catalog based on BSI G0 list with 47 elementary threats;
- Possibility to create custom threats;
- Assigning additional controls to threats and their monitoring, plus the connected requirements.
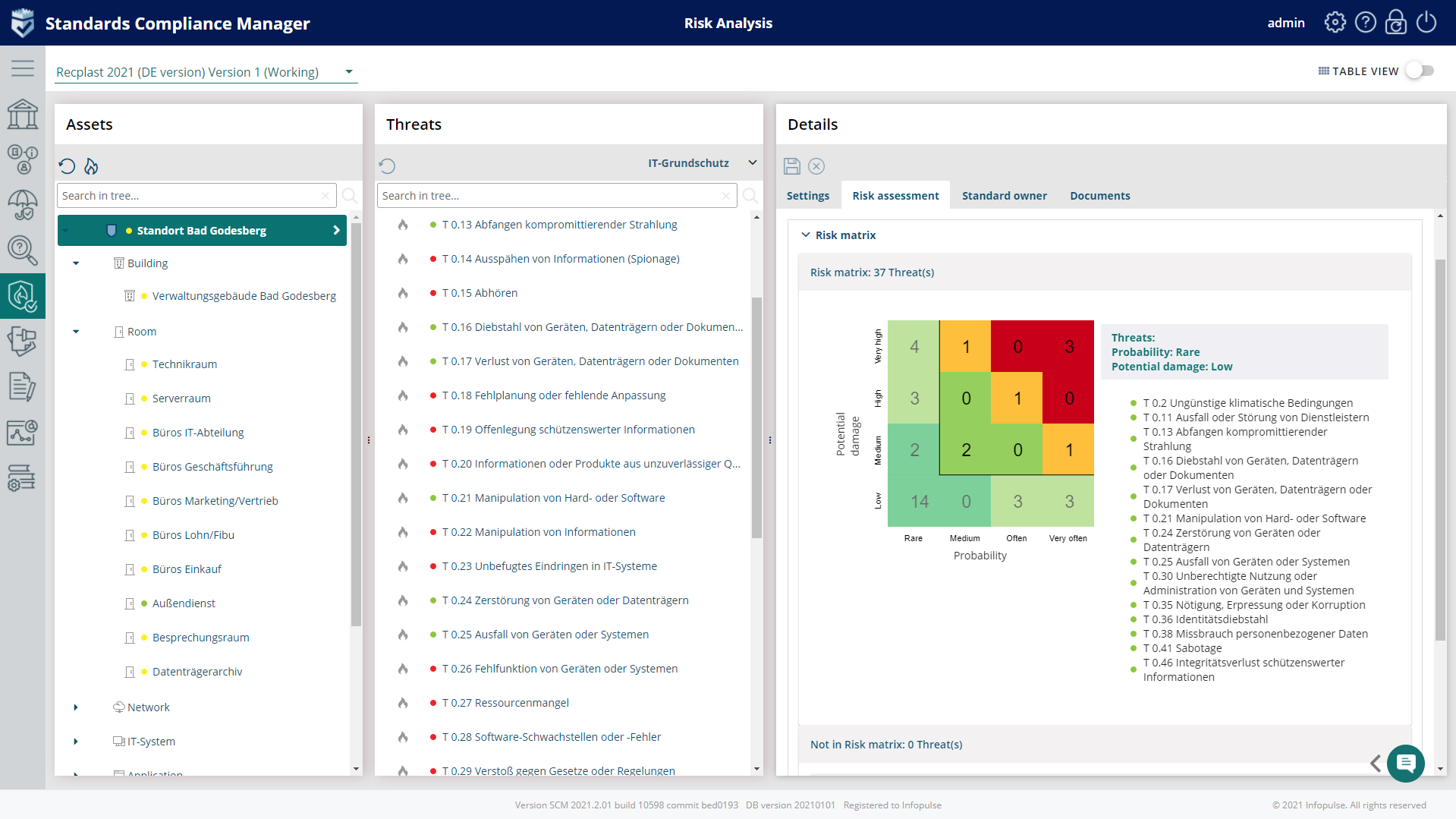
3. Risk Classification
It provides an overview of the risks associated with threats to specific targets.
Risk assessment refers to the threats and damage scenarios: potential damage, probability, and risk category.
BSI defines the risk analysis matrix to illustrate the risk characterization adapted to the individual needs. It includes the risk categories (low, medium, high, very high) and frequency of occurrence.
In Compliance Aspekte, you can work with the risk analysis matrix (4×4 or 5×5 dimension) to holistically view the threat probability and its impact on each asset and quickly identify those threats requiring urgent treatment.
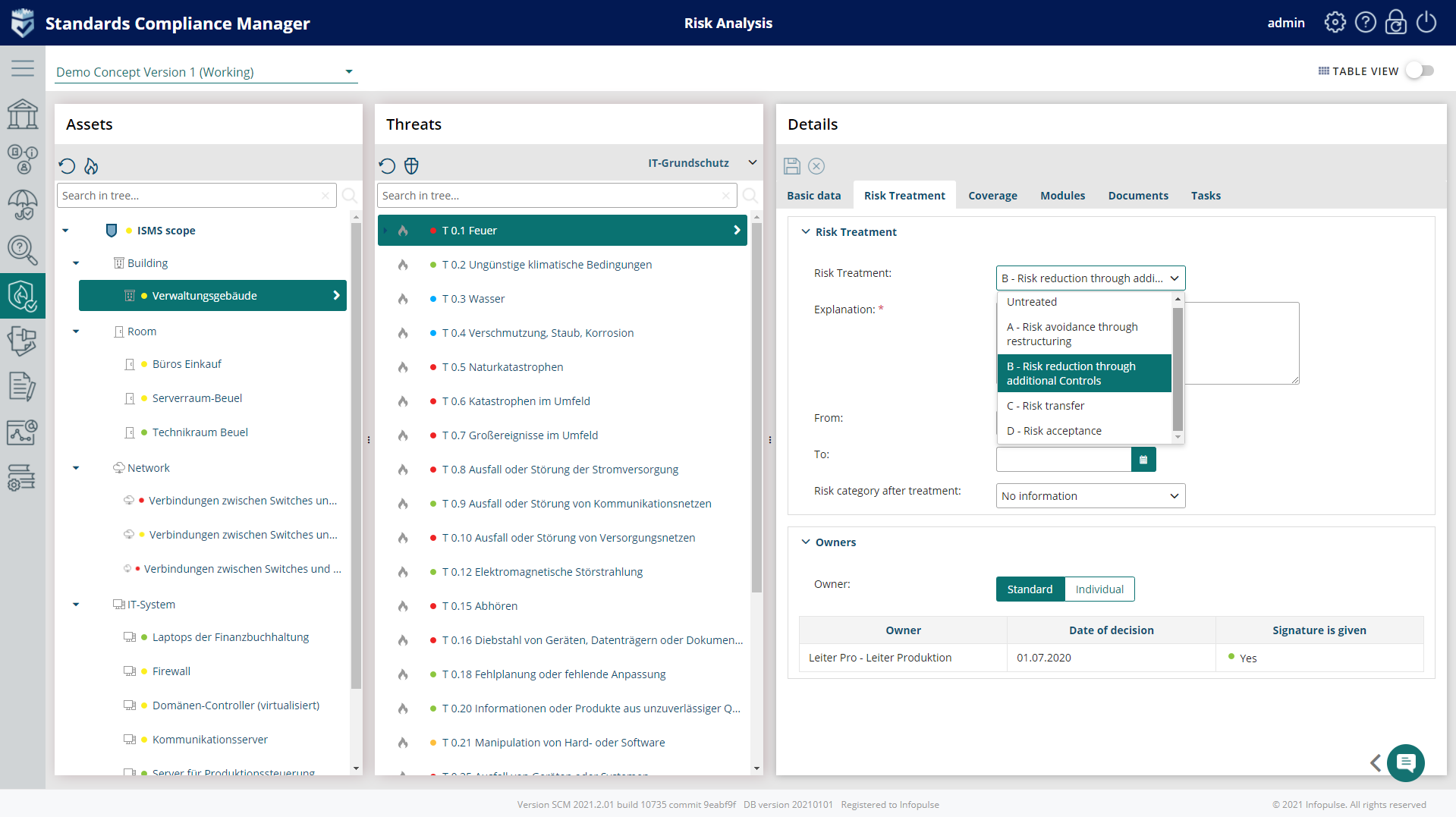
4. Risk Treatment
After you have defined and assessed your risks, in this stage, you will select treatment options:
- Accept the risk;
- Mitigate it by reducing any risk found in physical, technical, or administrative systems or controls by taking action;
- Avoid the risk – remove any compromised assets;
- Transfer the risk – assign it to another party;
- Share it with third parties by assigning informational assets components or certain processing activities to external stakeholders.
Compliance Aspekte allows to:
- Define Risk mitigation measures and map them to requirements and controls;
- Accept risks automatically;
- Bulk edit selected Threats;
- Set up deadlines for risk treatment;
- Assign additional controls, the connected requirements to threats, and monitor them.
5. Risk Monitoring
Threats are identified as acceptable, but their occurrence may increase in the future require further action, and are usually set for monitoring. Companies usually develop additional security controls to use if the risks become unacceptable.
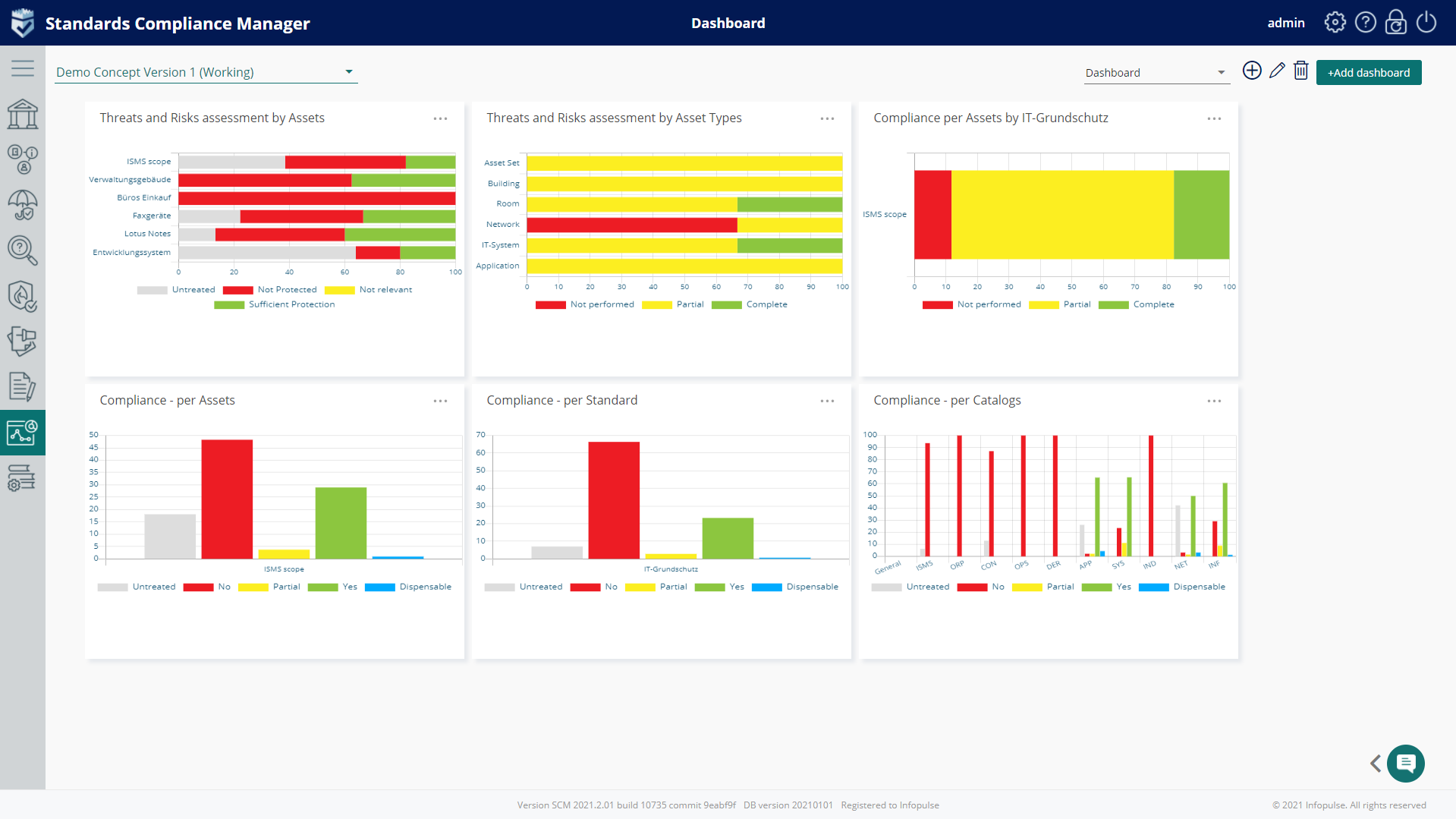
The detailed record of monitoring history for project risk management is available on the dashboards of the Compliance Aspekte.
The solution enables you to generate standard reports (A1-A6) according to IT-Grundschutz and provides a framework for covering industry-specific security standards (B3S) and IT-Grundschutz profiles.
Compliance Aspekte risk management tool is easy to use and a risk mitigation-focused tool. Please contact us to get a demo and a free non-binding 3-MONTHS test.
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
