How vulnerable our Systems are?
It is about organizational and technical security aspects.
Organizational aspect involves security practices, processes, policies, and standards implemented in all organization processes. It also includes the security hygiene and behavior of every employee within the organization. This is the primary level of protection.
Technical aspect relates purely to technology. Putting it very simply: bugs in the code, insecure environments, low-protected networks, poor password management, and… hundreds and hundreds of unsafe software development habits that finally land in your organization.
This article relates to the information security of the entire organization including people, processes, and technical vulnerabilities of corporate infrastructure, websites, or user applications.
Vulnerabilities in People
We can look at Vulnerability as a loophole in the system allowing an attacker to cause damage to your assets. In most cases, humans are the weakest link in the chain. The ever-growing number of social engineering and scamming tricks artfully targeted at human foibles, desires, or fears practically meet no resistance.
So the assessment of your organization’s vulnerabilities and associated risks always includes the human factor. Let see a little bit statistic on this.
The Scam Watch Radar of the Australian Competition and Consumer Commission (ACCC) provides overwhelming stats about the scams pulled on individuals daily nationwide. The fact worth mentioning is that the prevailing delivery methods are phone and email.
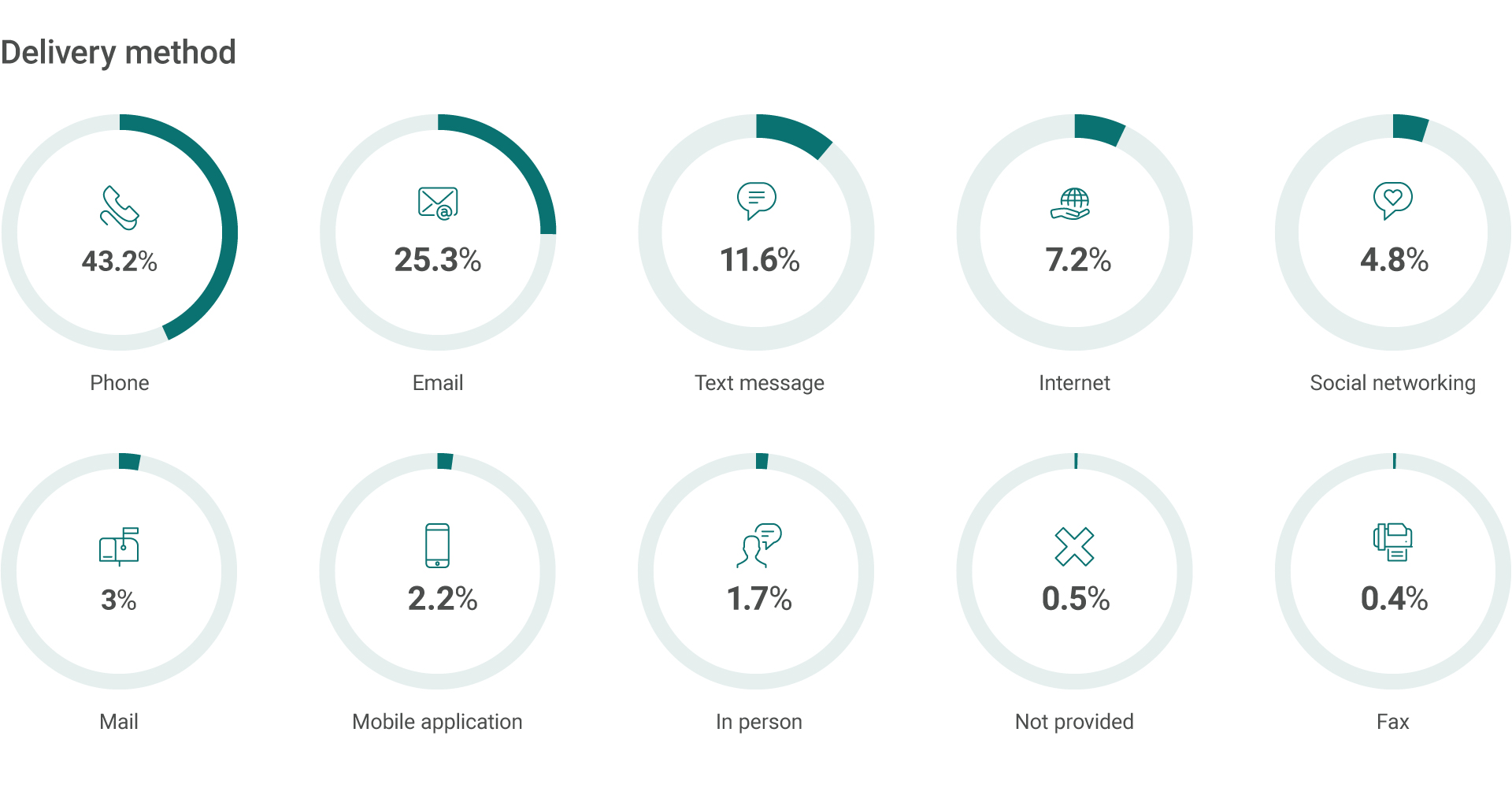
We are of a strong opinion that security in an organization starts with its employees. Today, information security is no longer a business of IT departments only. It is everyone’s concern, from top to bottom. The highest and the lowest rank employees are the Target No. One. The former are the most lucrative catch, while the latter are the easiest to get through.
Inviting all employees to an annual CISO’s cybersecurity report meeting and getting them regularly sign new policies do not work. It is about grow a mature security culture. It is about getting everyone truly engaged into a new paradigm of the Digital Age: cyber protection of your environment begins with you personally.
This can be achieved through teaching the employees to be responsible for the common security and cultivate correspondent skills. Teach them to stay alert and follow secure practices continuously not because it is a requirement from authority. Because this is the only way to maintain the organization’s security.
To add one more detail that is important: invite experts to test and train your employees to resist the effective methods of social engineering.
Vulnerabilities in Processes
National and international standards related to information security ISO 27K series, IT-Grundschutz, GDPR, etc., provide detailed guidance on building secure ecosystems. However, implementing and maintaining compliance with the standards is a challenging task for any organization regardless of its size.
First, it is due to complexity and versatility of requirements. To take off from the scratch translates into significant cost and effort. On the early stage, expert advice is an invaluable contributor to put things right from the start.
Failing to follow the best security practices creates much risk that vulnerabilities in the inappropriately established processes would pile up in a blink of the eye.
The highly recommended approach includes using automated solutions. They have a range of obvious benefits:
- Create a clear path to achieving your security objectives
- Eliminate silos, double-entries and responsibility overlapping
- Reduce cost, and free resources
- Put you in the control of every detail of organization’s security and compliance
- Simplify compliance management
- Minimize the possibility of human error
Besides, compliance platforms like Compliance Aspekte provide a variety of convenient features for risk assessments, real-time control, reporting, auditing and so on.
Vulnerabilities in Infrastructure
Certain compliance activities are also aimed at security of infrastructure. They include having the most recent versions of operating systems, all applications timely patched and updated, proper access and password management procedures in place, etc. These organizational measures are surely not enough.
International organizations like OWASP unite the efforts and expertise of security professionals worldwide around the web applications security risks. They provide guidance, tools, cheat sheets, videos and extensive conferences to anyone interested in improving application security.
The list of app vulnerabilities is huge. Here are a few examples:
- SQL, NoSQL, OS, and LDAP injection
- Cross Site Scripting (XSS)
- XML External Entities (XXE)
However, checking your software and hardware for known vulnerabilities is another challenge on the way to a secure system. This task is for highly qualified security professionals with hands-on experience in dependency analysis and penetration testing, have correspondent tools and relevant proved techniques. If in your organization there are no specialists of this level, you can outsource this service from reputable security providers.
Dedicated Information Security Services
Compliance Aspekte helps its customers to identify all the potential threats and existing vulnerabilities in their system.
Our most often demanded services include:
- Penetration Testing, including Social engineering
- Source Code Analysis
- Assistance in Security Audit Preparation
- Risk Assessment
The Compliance Aspekte security experts detect and identify security flaws, threats and related risks providing you with recommendations on the improvement embedded into a complete action plan.
Contact the Compliance Aspekte security experts to find out how firm your system stands on the ground. Individual objectives, holistic approach, and 100% reliable result.
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
