Building an Efficient Security Compliance Strategy. Part 2: Practical Steps

Proper maintenance of an organization’s information security management system (ISMS) is the key to the protection of your sensitive information and valuable assets. As we have described in Building an Efficient Security Compliance Strategy. Part 1, companies face many challenges when establishing and maintaining security compliance strategies.
We continue our information security journey and will guide you through a step-by-step ISMS implementation on the basis of IT-Grundschutz.
ISMS via IT-Grundschutz
Following IT-Grundschutz, you will be able to appropriately build an ISMS and protect your organization. This regulation provides users with standardized security recommendations and clearly outlined implementation steps collected in the Compendium.
IT-Grundschutz Compendium in combination with modern governance, risk, and compliance solution make it easier for security and data protection officers to maintain information security (IS) in their day-to-day work.
It is essential not only to focus on the security of IT systems, but also pay attention to the technical, organizational, infrastructural, and personnel aspects. The security of the operating environment, the reliability of services, proper handling of the information, and many other important things should also be taken into account.
Three Steps of Establishing an effective ISMS based on IT Grundschutz
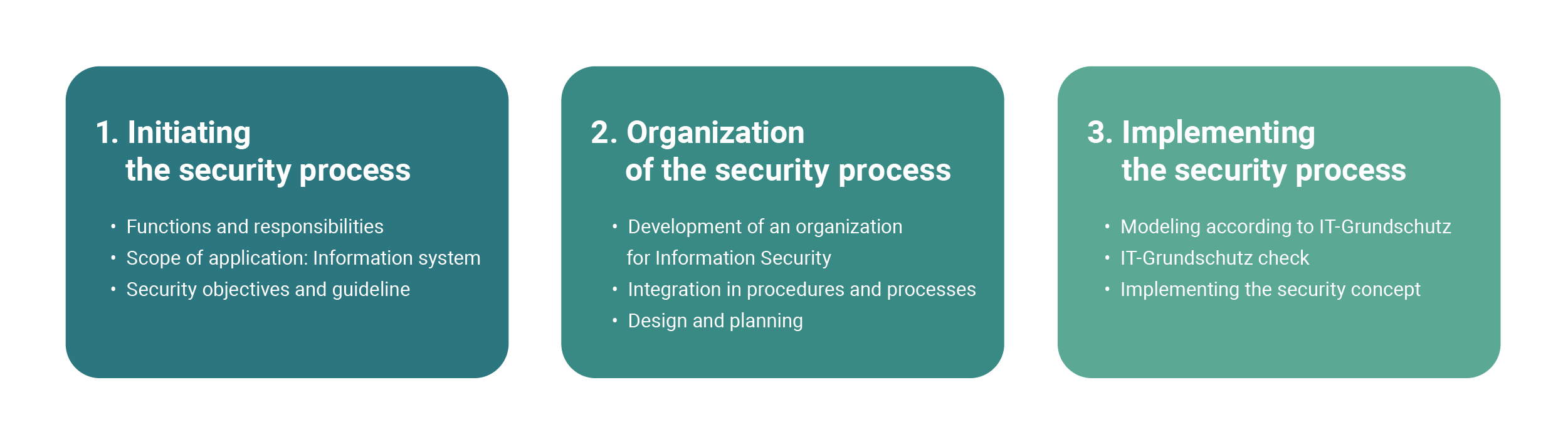
1. Starting the Security Process
- Governance. Ensure that the company’s management board understands the necessity and importance of the ISMS and offers assistance at all levels.
- Responsible Person. Company management should consider an appointment of a chief information officer (CISO) who will be responsible for guiding and working with the ISMS. Data Protection Officer (DPO) can be assigned to accompany all aspects of data protection within an organization and introduce appropriate control mechanisms. Without someone capable of performing the IT security compliance program, the whole plan will be hard to implement.
- Integration of All Employees into the Security Process. Conducting practical training and education of the CISO, DPO, IT security managers, and all people involved in the security compliance process is a must. It will ensure better workflow and cooperation between all the parties involved.
- Planning the Security Process: Define the Scope. Establishing a continuous information security process and defining an appropriate strategy. The company management should set basic security objectives and the level of IS to align with the business goals. During this phase, analyze stakeholders (i.e., the relevant internal and external parties), business objectives, tasks, and security requirements.
It is vital to determine the IS goals at the very beginning of each security process so that the security strategies and concepts match the actual requirements of the company.
2. Organization of the Security Process
- Establish the Organization for Information Security. The structure of the company should promote and implement the information security process. The organization of IS depends on the size, nature, and structure of the particular business.
- Integrate Information Security in All Organization Processes. Information security must be integrated into the processes within the overall organization, and contact persons must be specified. Take into account all the necessary security aspects in all strategic decisions at an early stage.
- Design the Security Process. Identify all the conditions for your IS to be implemented and the level of information security required for your company. IT-Grundschutz offers three approaches to IT protection to follow: basic, standard, and core.
3. Implementation of the Security Process
- Create a Concept. Draw up a concept according to any type of protection approaches based on IT Grundschutz. Define the security concept, decide which data must be protected and prioritize.
- Inventory Analysis. Define all your existing assets that must be protected. IT-Grundschutz provides you with detailed requirements and controls for your valuable objects.
- Compliance Check. After you have all your assets defined, you will check your project’s current compliance status. Go through each requirement for every asset and access the implementation details and threats provided by IT-Grundschutz Compendium.
- Risk Analysis. During this phase, you will use the modeling in line with IT-Grundschutz to assess risks in a structured manner and take corresponding security measures. According to IT-Grundschutz, there are three ways you can respond to the risk: 1) Treat the risk by applying controls; 2) Terminate the risk by avoiding it; 3) Transfer the risk to third parties.
- Documentation of Results: Reporting. Document the results of the risk analysis, as you will be able to use them as the basis to address the requirements and measures where the gaps still exist.
- Audit. The audit is an integral part of any security implementation process. You can conduct internal and external audits within the company to see all the potential ISMS gaps. It is the final stage of preparation for certification.
- Certification. The last step is, obviously, to have your ISMS examined and certified by the Federal Office for Information Security. You can be certified according to ISO 27001 on the basis of IT-Grundschutz.
Continual Improvement
For your ISMS to be effective, it is not enough just to implement appropriate security safeguards and update documents. You should take an approach to the continuous improvement of the information security process. The information security audit is an essential part of your ISMS and is integrated into the “Check” phase of the PDCA model.
It is essential to trace success, make appropriate evaluations, and hold meetings after serious security incidents happen or if there are serious changes to the framework conditions. Document all results and decisions.
We at Infopulse follow the Plan-Do-Check-Act cycle predefined by ISO 27001 to achieve the continual improvement model that starts right after the audit. First, you plan your ISMS and then implement it. Next, you check the performance of your new arrangements and decide if they are achieving what you had intended or can be further enhanced. Finally, you act upon those decisions, beginning another PDCA cycle as you implement the improvements.
Managing Your Security Management System with the GRC Solution
To make your information security procedures more holistic, you may use a relevant GRC solution that will enforce automation and make your compliance routine easier, more reliable, and faster.
Key Beneficial Features of SCM for IS
Implementing BSI IT-Grundschutz you will be able to:
- Create concepts, perform inventory and compliance checks as well as risk analysis, consider all the gaps, risks, and safeguards available.
- Use the IT-Grundschutz and Compendium integrated into the system and access all the relevant updates with the newly issued version.
- Migrate from the old version of IT-Grundschutz to the new one with one click.
- Easily manipulate, arrange, bulk-edit, sort, and filter the data during inventory and compliance checks, risk management analysis;
- Generate standard GS reports;
- Fully automate the report generation process thanks to the SCM Bot and then send them at a specific time via email to the defined persons involved.
With Infopulse SCM, you will be able to achieve the most efficient implementation of the intended security measures.
Bring your compliance to the next level with Infopulse SCM!
Try Compliance Aspekte For Free
Book a 1-2-1 Live Demo and Obtain a 3-months Non-binding Trial
Effective and easy-to-use IT security management system based on the latest standards and regulations — from planning and establishing the security concept to certification.
